Beginner’s Guide to Mock API for Authentication Testing

Your lightweight Client for API debugging
No Login Required
Requestly is a web proxy that requires a desktop and desktop browser.
Enter your email below to receive the download link. Give it a try next time you’re on your PC!










Authentication testing involves expiring tokens, renewing sessions, and validating role-based access. Running these scenarios against live services is unreliable because tokens time out, rate limits interfere, and third-party providers behave inconsistently across environments.
A mock API for authentication testing solves this by simulating authentication flows in a controlled setup. It allows teams to reproduce success and failure cases on demand, validate token lifecycles, and test permission rules without depending on unstable or incomplete backends.
This article explains how a mock API for authentication testing works, why it is useful, and the steps to implement it effectively.
What Is a Mock API for Authentication Testing?
A mock API for authentication testing is a simulated version of authentication endpoints used during development and testing. Instead of connecting to real identity services or backends, it returns predefined responses that imitate how those services behave.
The goal is not to replace the actual authentication system but to give testers control over scenarios that are hard to reproduce in production. For example, triggering an “invalid token” or “account locked” error on demand is difficult with a live API, but with a mock, these outcomes can be scripted and tested consistently.
At its core, a mock API for authentication testing:
- Accepts requests in the same format as the real authentication service
- Returns predictable responses such as valid tokens, expired tokens, or error codes
- Mimics workflows like login, logout, session refresh, or role assignment
- Runs locally or in test environments, independent of production dependencies
Benefits of Using a Mock API for Authentication Testing
The main advantage of a mock API for authentication testing is control. Live authentication systems are unpredictable, but a mock lets testers decide exactly how the service should respond. This control makes testing faster, more reliable, and easier to repeat.
Here are the key benefits that stand out when using a mock API for authentication testing:
- Consistent Test Scenarios: Authentication errors such as expired tokens or invalid logins can be simulated on demand. This ensures the same conditions can be tested repeatedly without relying on real-world timing or third-party responses.
- Faster Development Cycles: Teams do not need to wait for a backend or third-party identity provider to be available. Frontend and backend components can be developed and tested in parallel.
- Wider Test Coverage: Scenarios that are difficult or risky to test with a live service, such as brute force login attempts or sudden session terminations, can be covered with a mock API.
- Reduced External Dependency: A mock API removes rate limits, downtime, or unpredictable changes from third-party services, keeping tests stable across environments.
- Early Bug Detection: Authentication flaws in session handling or role validation are found earlier, before integration with production systems.
Core Components of a Mock API for Authentication Testing
A mock API for authentication testing is effective only when it reproduces the critical behaviors of real authentication systems. These behaviors revolve around how requests are made, how responses are generated, and how different conditions are controlled.
Below are the core components that define a reliable mock API for authentication testing:
- Endpoint Simulation: The mock should expose endpoints that mirror real authentication services, such as /login, /logout, or /refresh-token. This ensures applications can switch between mock and live services without changing request formats.
- Predefined Responses: Responses need to be configurable so testers can simulate success, failure, or edge cases. For example, a login request can return a valid token, an expired token, or an error message depending on the test case.
- Token Management: Authentication revolves around tokens. The mock must be able to generate, invalidate, and refresh tokens in ways that reflect real-world behavior, including expiration times and invalid token scenarios.
- Role and Permission Handling: Many applications rely on role-based access. A mock API should support different user roles, such as admin or standard user, and enforce access rules so these flows can be tested.
- Error Injection: To validate how an application reacts under failure conditions, the mock should allow controlled errors such as timeouts, 401 unauthorized responses, or malformed tokens.
- Environment Control: The mock should be deployable locally or in a test environment. This flexibility helps teams run automated tests without dependency on external services.
How to Create a Mock API for Authentication Testing
Creating a mock API for authentication testing means building endpoints that act like a real service but give testers complete control over responses. This can be achieved either with in-house setups or with dedicated mocking tools.
Here are the steps involved in creating a mock API for authentication testing:
Step 1: Define authentication flows
List the exact flows that need coverage, such as login, logout, token refresh, and role validation. Having clarity on these flows ensures that the mock reflects the behavior of the real service.
Step 2: Set up endpoints
Build endpoints that match the structure of the live authentication API. For example, /login should accept credentials and issue a token, while /refresh-token should renew tokens once they expire.
Step 3: Configure responses
Prepare both success and error responses. A valid login should return an access token with an expiration time, while invalid credentials, expired tokens, or locked accounts should return error codes like 401 or 403.
Step 4: Implement token logic
Design the mock to generate tokens with expiration times, enforce validity rules, and allow simulation of expired or invalid tokens. This ensures token lifecycles are tested thoroughly.
Step 5: Add role and permission controls
Include role-based responses. For example, an admin role should access restricted routes, while a standard user should receive a forbidden response when attempting the same action.
Step 6: Enable error simulation
Introduce configurable errors such as delayed responses, timeouts, or malformed tokens. This helps test how the application responds under failure conditions.
Step 7: Integrate with the test environment
Run the mock locally or in a staging setup so automated and manual tests can interact with it. This makes it possible to test consistently without relying on external services.
Advanced Considerations in Authentication Mocking
In real-world applications, authentication often involves more complexity. Advanced considerations ensure that a mock API not only handles surface-level cases but also reflects scenarios closer to production systems.
1. Token Types and Expiration
Most systems use JWTs (JSON Web Tokens) or opaque tokens. JWTs are commonly used because they carry encoded user claims, roles, and expiration details. A good mock should allow simulation of both valid and invalid JWTs.
For example, a valid JWT can be generated with a library like jsonwebtoken in Node.js:
const jwt = require('jsonwebtoken');
const token = jwt.sign(
{ userId: "12345", role: "admin" },
"mock-secret-key",
{ expiresIn: "15m" }
);
Testers can then simulate expired or tampered tokens by adjusting the expiresIn value or modifying the payload. This allows them to check how the system behaves when tokens are invalidated mid-session.
2. Multi-Factor Authentication (MFA)
Modern applications often enforce MFA. A mock API can replicate MFA by requiring a second step after login, such as an OTP (One-Time Password). The mock can return a response like:
{
"status": "MFA_REQUIRED",
"message": "Enter the 6-digit code sent to your device"
}
By scripting different OTP outcomes (valid, expired, or incorrect), testers can validate whether the application handles MFA correctly without needing an actual SMS or email service.
3. Role-Based Access Control (RBAC) and Claims
Real systems often enforce access rules at multiple levels: some APIs are available to all users, while others are restricted to admins or premium users. A mock API should issue tokens with claims that reflect these roles.
For example:
{
"token": "eyJhbGciOiJIUzI1NiIsInR...",
"claims": {
"role": "standard_user",
"permissions": ["read_profile"]
}
}
This setup allows testing how endpoints behave when a user tries to access a resource they do not have permission for.
4. Simulating Network and Service Failures
Authentication issues are not always logical errors. They can also be caused by network delays, timeouts, or service unavailability. A mock API should let testers deliberately inject these conditions. For instance:
app.post("/login", (req, res) => {
setTimeout(() => {
res.status(500).json({ error: "Authentication service unavailable" });
}, 3000); // simulate network delay
});
This helps validate if the application retries correctly, shows proper error messages, or fails gracefully under stress conditions.
5. Testing Refresh Token Rotation and Replay Prevention
Many modern systems don’t just issue static refresh tokens. Instead, they rotate tokens every time they’re used. Once a refresh token is used, it should become invalid, and a new one must be generated. This prevents token replay attacks.
A strong mock API should:
- Invalidate old refresh tokens once they are used.
- Generate new refresh tokens for every refresh request.
- Reject reuse of the same refresh token with a 401 Unauthorized error.
Example mock logic (Node.js/Express):
let validRefreshTokens = new Set();
app.post('/refresh-token', (req, res) => {
const { token } = req.body;
if (!validRefreshTokens.has(token)) {
return res.status(401).json({ error: 'Invalid refresh token' });
}
// Invalidate old token
validRefreshTokens.delete(token);
// Issue new tokens
const newAccessToken = generateToken();
const newRefreshToken = generateRefreshToken();
validRefreshTokens.add(newRefreshToken);
res.json({ accessToken: newAccessToken, refreshToken: newRefreshToken });
});
This allows testers to validate whether client apps handle token rotation correctly.
6. Testing Session Revocation Across Devices
In enterprise setups, users may log in from multiple devices. If one session is revoked (for example, logging out from all devices after a password reset), all related tokens should become invalid.
To simulate this in a mock API:
- Maintain a mapping of users to active sessions.
- When a global logout is triggered, invalidate all tokens for that user.
- Ensure subsequent requests with old tokens return a 403 Forbidden error.
This scenario ensures testers can verify that applications respect global logouts and don’t allow stale sessions to remain valid.
7. Multi-Factor Authentication (MFA) Flow Simulation
Basic mocks usually stop at username and password. But in many real systems, login also requires MFA like OTP, SMS codes, or authenticator apps.
A realistic mock API should:
- Provide an additional step after password verification.
- Return a status like “MFA_REQUIRED” before issuing tokens.
- Accept and validate OTPs or temporary codes before final login success.
Example response pattern:
// First login attempt
{
"status": "MFA_REQUIRED",
"mfaType": "TOTP"
}
// After OTP is provided
{
"accessToken": "new-token",
"refreshToken": "new-refresh-token",
"expiresIn": 3600
}
This helps test whether clients handle MFA prompts correctly and whether automated test flows can mimic both success and failure paths of MFA validation.
Common Challenges in Mock API for Authentication Testing
Mock APIs are effective for controlling authentication flows during testing, but they come with their own set of challenges. These issues usually appear when mocks are either too simple or not aligned with how authentication works in real environments. Below are the most common challenges teams face:
- Oversimplified authentication logic: Many mock APIs only return a success token without implementing realistic checks like scope validation, token expiry, or refresh flows. This creates a gap between test results and real-world behavior.
- Inconsistent mock behavior: If different teams or pipelines configure authentication mocks in separate ways, the application may pass in one setup but fail in another. Lack of consistency undermines trust in test results.
- Ignoring negative test cases: Teams often focus only on valid login flows. Missing tests for invalid credentials, expired tokens, or revoked sessions lead to incomplete coverage and hidden vulnerabilities.
- Outdated or unmaintained mocks: Authentication standards evolve quickly, and mocks that are not updated to reflect changes in OAuth2, JWT, or OpenID Connect can mislead developers and testers.
- Difficulty scaling across environments: A mock that works locally may not behave the same way in CI/CD pipelines if configuration files, environment variables, or certificates are not aligned.
Best Practices for Mock API for Authentication Testing
A mock API is only valuable if it reflects real-world behavior and remains reliable across different testing stages. Poorly designed mocks can hide authentication flaws instead of exposing them. To avoid these pitfalls and ensure long-term value, consider the following best practices:
- Align with real authentication standards: Follow OAuth2, JWT, or OpenID Connect conventions instead of inventing simplified flows. This ensures the application tested against the mock behaves similarly when connected to a live identity provider.
- Keep token lifecycles realistic: Simulate expiration for access and refresh tokens. For example, use short-lived access tokens and enforce refresh flows so that token renewal logic is validated.
- Support multiple test paths: Authentication should fail as often as it succeeds in testing. Simulate incorrect credentials, missing headers, and expired tokens so the system is tested against both valid and invalid scenarios.
- Separate test data from real data: Use only synthetic usernames, passwords, and token payloads. This avoids security risks and prevents confusion with production accounts.
- Automate mock setup and configuration: Define authentication rules, endpoints, and responses in configuration files or scripts. This ensures the mock can be reused consistently across local development and CI/CD pipelines.
- Version and document the mocks: Authentication logic changes frequently. Keep mock APIs under version control and document expected responses, error codes, and flows. This prevents a mismatch between developer assumptions and test behavior.
Why Use Requestly for Mock API for Authentication Testing
Requestly by BrowserStack is a network debugging and API simulation platform that helps developers and testers create controlled authentication scenarios. Instead of waiting for a live identity provider, teams can mock login flows, manipulate tokens, and test both valid and invalid responses directly within their workflow.
Here are the key features that make Requestly effective for authentication testing:
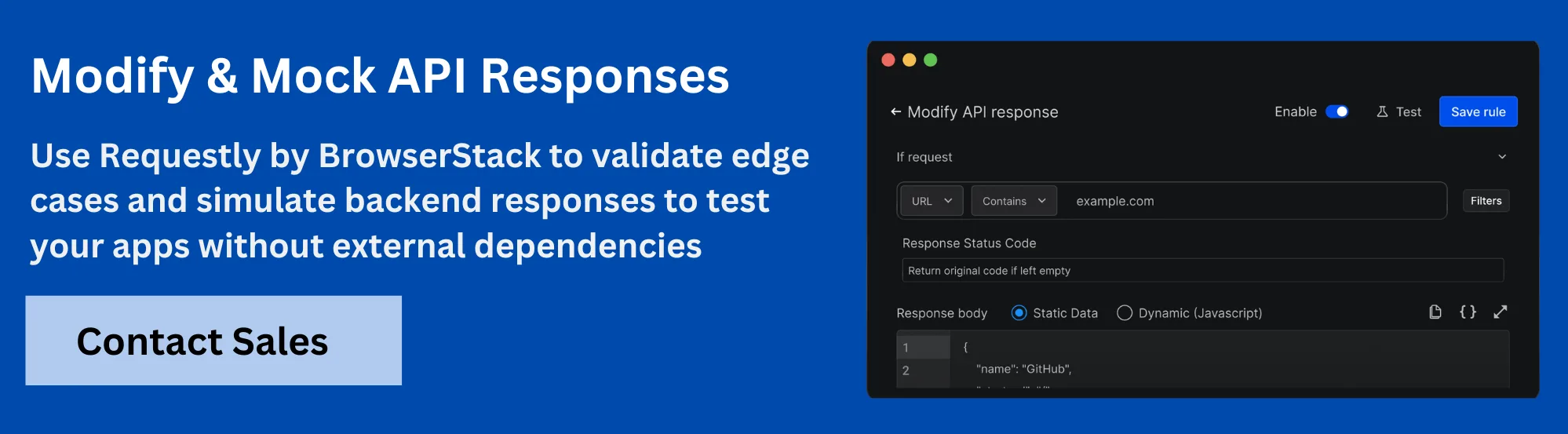
- Modify API responses: Return customized responses such as expired tokens, invalid credentials, or permission errors to test negative paths.
- Modify request body and headers: Inject authentication headers, alter request payloads, or simulate missing credentials to verify request handling.
- Modify HTTP status codes: Replicate authentication-related responses like 401 Unauthorized or 403 Forbidden without a backend dependency.
- HTTP interceptor: Intercept, record, and debug requests to confirm that authentication flows are correctly triggered and handled.
- Cross-device testing: Validate how authentication behaves across different devices and environments, ensuring consistent behavior beyond local setups.
Conclusion
Mock APIs make authentication testing faster and more reliable by simulating login flows, token lifecycles, and failure scenarios without relying on external identity providers. They reduce delays in development and give teams the confidence that authentication will behave consistently under real-world conditions.
Requestly extends these benefits with purpose-built features for mocking authentication. Its ability to create mock endpoints, manipulate responses, and simulate token behavior enables teams to test complex scenarios with precision while keeping workflows consistent across environments.

Contents
- What Is a Mock API for Authentication Testing?
- Benefits of Using a Mock API for Authentication Testing
- Core Components of a Mock API for Authentication Testing
- How to Create a Mock API for Authentication Testing
- Advanced Considerations in Authentication Mocking
- 1. Token Types and Expiration
- 2. Multi-Factor Authentication (MFA)
- 3. Role-Based Access Control (RBAC) and Claims
- 4. Simulating Network and Service Failures
- 5. Testing Refresh Token Rotation and Replay Prevention
- 6. Testing Session Revocation Across Devices
- 7. Multi-Factor Authentication (MFA) Flow Simulation
- Common Challenges in Mock API for Authentication Testing
- Best Practices for Mock API for Authentication Testing
- Why Use Requestly for Mock API for Authentication Testing
- Conclusion
Subscribe for latest updates
Share this article
Related posts
Get started today
Requestly is a web proxy that requires a desktop and desktop browser.
Enter your email below to receive the download link. Give it a try next time you’re on your PC!