The Beginner’s Guide to APIs: Types, Benefits, and Protocols

APIs, short for Application Programming Interfaces, define how two software components interact. They act as an interface between systems, allowing one application to use another’s data or functionality. Instead of accessing the database or internal logic directly, developers can use APIs to request only the specific data or action they need.
At their core, APIs allow systems to communicate using a common language. They manage requests and responses in a standardized way, which reduces complexity, improves efficiency, and supports faster development and integration across different platforms.
This article explains what an API is, the different types and communication protocols used, and how they help connect and secure systems.
What is an API?
An API, or Application Programming Interface, is a defined set of rules that allows one software application to communicate with another. It specifies how requests should be structured, what data can be exchanged, and how responses are returned.
APIs act as a controlled interface between systems. They enable applications to access functionality or data from other systems without exposing internal code or underlying processes. This ensures interactions remain predictable and secure, while also allowing different platforms and technologies to work together efficiently.
Benefits of Using APIs
APIs provide a structured way for applications to communicate, which brings several tangible advantages for developers and businesses.
Below are the main benefits of using APIs:
- Faster Development: APIs let developers leverage existing services, avoiding the need to recreate core functionality. For example, using a payment gateway API saves months of backend work and compliance setup.
- Improved Efficiency: By directly sharing data between systems, APIs reduce manual processes, repetitive coding, and the risk of inconsistent data across platforms. This is particularly important in large enterprises where multiple applications need synchronized information.
- Scalability: APIs allow systems to scale independently. A backend service can handle increasing traffic without requiring all connected applications to be redesigned, supporting growth without disrupting existing workflows.
- Consistent User Experience: Standardized API responses ensure that different applications consuming the same service behave predictably. For example, mobile and web apps using the same API deliver uniform content and functionality.
- Security and Access Control: APIs offer built-in mechanisms for authentication, authorization, and monitoring. This protects sensitive data while still enabling third-party integrations or internal automation.
- Enabling Innovation: APIs allow businesses to expose services to partners or external developers safely. This creates opportunities for new features, integrations, and products without impacting the core system.
Different Types of APIs
APIs vary based on how they are used, who can access them, and how they exchange data. Below is a detailed look at the main API types with real-world examples.
1. Web APIs
Web APIs allow applications to communicate over the internet using standard protocols like HTTP or HTTPS. They expose specific endpoints that accept requests and return structured responses, often in JSON or XML format. Web APIs are commonly used for integrating services without requiring direct access to underlying systems.
Example: A weather app uses a web API to get live temperature and forecast data from a weather service. The app sends a request specifying the city, and the API returns only the relevant weather data.
2. RESTful APIs
RESTful APIs follow the Representational State Transfer (REST) design principles. They operate over HTTP using methods such as GET, POST, PUT, and DELETE, each corresponding to a specific operation on a resource. REST APIs are stateless, meaning each request contains all the information needed to process it.
Example: An e-commerce website uses RESTful APIs to retrieve product listings, update inventory, and process orders. Each API call is independent, allowing multiple applications or devices to access the same backend seamlessly.
3. SOAP APIs
SOAP, or Simple Object Access Protocol, exchanges data in XML format and follows strict standards for security, reliability, and error handling. SOAP APIs support complex operations and transactional processes, making them suitable for industries where accuracy and compliance are essential.
Example: Banks use SOAP APIs to process secure fund transfers. The protocol ensures that each transaction is logged, validated, and encrypted, reducing errors and fraud risks.
4. GraphQL APIs
GraphQL APIs allow clients to specify exactly what data they need, reducing over-fetching or under-fetching. Unlike REST, a single endpoint can serve multiple types of queries, making it flexible and efficient. This is particularly useful for applications with variable data requirements or limited bandwidth.
Example: A social media app uses GraphQL APIs to fetch a user’s name and profile picture for a feed. The same API can also be used to retrieve posts, comments, or likes as needed, all from a single query.
5. Public APIs
Public APIs are accessible to any external developer and encourage third-party integrations. They are used to expand functionality, create ecosystems, or allow external developers to build on top of a platform. Public APIs usually come with usage limits and authentication keys.
Example: Google Maps provides public APIs to embed maps, routes, and location services into third-party websites or mobile apps, enabling external applications to leverage Google’s location data.
How APIs Facilitate Communication Between Systems
APIs enable systems to exchange data and functionality in a controlled and predictable way. They act as an intermediary that defines how requests should be made, what data can be shared, and how responses are returned. This structure allows different applications to work together without direct access to each other’s internal logic.
The process of API communication can be broken down into the following steps:
- Client Initiates Request: A system or application (the client) identifies the operation it needs from another system. It prepares a request containing the endpoint, method, headers, and any necessary data.
- Request Sent to Server: The client sends the request over the network, typically using protocols like HTTP or HTTPS. The API endpoint on the server receives this request.
- Server Processes Request: The server interprets the request according to the API rules. It validates authentication and authorization, retrieves or updates data, executes business logic, and prepares a response.
- Server Returns Response: The server sends a structured response back to the client, often using formats like JSON or XML. The response includes the requested data or confirmation of the action performed.
- Client Handles Response: The client parses the response and uses the data to update the user interface, trigger another operation, or perform further processing.
- Error Handling and Feedback: If something goes wrong, the server sends standardized error codes and messages. The client can then handle the error appropriately, such as retrying the request or showing a notification.
Key Protocols and Formats in API Communication
APIs rely on standard protocols and data formats to ensure systems can communicate accurately, securely, and efficiently. These protocols define how requests are sent, how responses are structured, and how clients and servers authenticate and exchange information.
Below are the key protocols and formats commonly used in API communication:
1. HTTP/HTTPS
HTTP (Hypertext Transfer Protocol) is the foundation for most web APIs. HTTPS adds a layer of encryption to ensure secure data transmission. APIs use HTTP methods such as GET, POST, PUT, and DELETE to perform actions on resources.
- GET retrieves data from the server
- POST sends new data to the server
- PUT updates existing data
- DELETE removes data
Using HTTP/HTTPS ensures that API requests and responses are standardized and can travel across networks reliably.
2. JSON
JSON (JavaScript Object Notation) is a lightweight, text-based format for structuring data. It is widely used in APIs because it is easy for humans to read and machines to parse. JSON allows nested objects, arrays, and key-value pairs, making it flexible for complex data structures.
3. XML
XML (Extensible Markup Language) is another format for exchanging structured data. It is more verbose than JSON but supports strict schemas, which can enforce rules for data validation. SOAP APIs typically use XML to ensure consistent structure and compliance.
4. OAuth
OAuth is an authorization protocol that allows applications to access resources on behalf of a user without sharing credentials. It provides a secure way to grant limited access to services, commonly used in public and partner APIs.
5. API Keys
API keys are unique identifiers assigned to clients to control and monitor access to an API. They help track usage, enforce quotas, and provide a basic level of security by ensuring only authorized applications can send requests.
Effective Strategies for API Integration
Integrating APIs effectively requires structured planning, proper implementation, and continuous management. Each step should focus on predictable behavior, secure data exchange, and maintainable workflows. Below are actionable strategies with concrete guidance.
- Map Endpoints and Data Flow: Identify the API endpoints you need, the data each returns, and how it fits into your application’s workflow. Determine which operations are synchronous versus asynchronous to avoid bottlenecks.
- Use Versioned Endpoints: Always connect to a specific API version. This ensures that updates or changes in the provider’s API do not break your integration. Implement mechanisms to switch versions deliberately when testing or upgrading.
- Validate Requests and Responses: Define schemas for request payloads and expected responses. For example, ensure numeric fields, date formats, and required keys match the API specification. Reject or log any unexpected data immediately to prevent downstream errors.
- Implement Robust Error Handling: Anticipate failure scenarios such as timeouts, rate limits, or invalid inputs. Include retry logic with exponential backoff, fallback operations, and structured logging for debugging and audit purposes.
- Optimize API Calls: Reduce unnecessary network requests by batching operations or caching frequent responses. Track response times and latency to identify endpoints that could affect performance.
- Enforce Strong Security: Always use HTTPS. Apply authentication mechanisms such as API keys, OAuth tokens, or JWTs. Restrict access to specific endpoints or operations based on roles, and monitor for suspicious activity.
- Monitor and Audit API Usage: Continuously track request counts, response times, error rates, and unusual patterns. Use monitoring to detect integration issues early and to plan for scaling or throttling needs.
Why API Security Matters
APIs process sensitive data and control core system operations. If they are not secured, attackers can steal data, manipulate transactions, disrupt services, or gain unauthorized system access.
Protecting APIs requires enforcing authentication to verify clients, applying authorization to restrict actions, encrypting all data in transit, and continuously monitoring activity for anomalies.
Key aspects of API security include:
- Authentication: Verify every client accessing the API using secure methods such as OAuth tokens, JWTs, or API keys. Ensure tokens expire appropriately and rotate credentials regularly.
- Authorization: Restrict what each authenticated client can do. Implement role-based or scope-based access to prevent unauthorized operations and enforce the principle of least privilege.
- Data Encryption: Encrypt all data in transit using HTTPS/TLS. For sensitive payloads, consider end-to-end encryption to prevent interception or tampering.
- Input Validation: Validate all incoming requests against strict schemas, including data types, lengths, and value ranges. Reject malformed or unexpected requests to prevent injection attacks and system corruption.
- Rate Limiting and Throttling: Define maximum request rates per client or endpoint. Prevent abuse, mitigate denial-of-service attacks, and protect server resources from overload.
- Logging and Monitoring: Record API activity including request metadata, response codes, and errors. Use real-time monitoring and anomaly detection to identify suspicious activity or breaches quickly.
- Regular Security Audits: Perform automated vulnerability scans, penetration tests, and code reviews. Ensure dependencies are updated and configuration errors are corrected to maintain a secure environment.
- Error Handling and Exposure Control: Avoid returning detailed system errors to clients. Provide only necessary information to prevent attackers from gaining insights into internal systems.
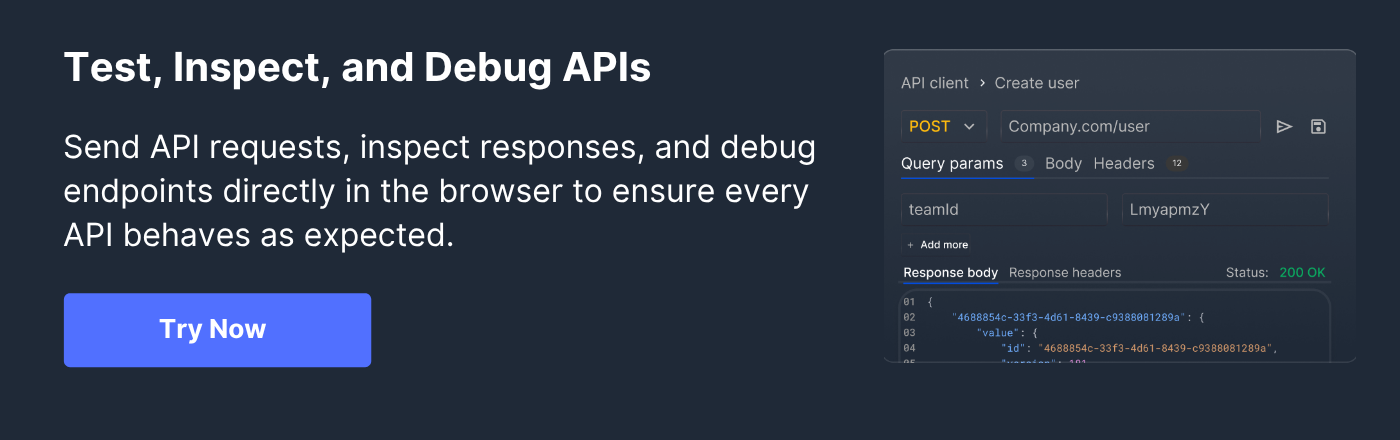
Why Use Requestly for API Testing
APIs can fail due to incorrect requests, misconfigured endpoints, or unexpected responses. Testing APIs thoroughly ensures they behave as expected and continue to work reliably as systems evolve.
Requestly provides tools to intercept, modify, and mock HTTP requests and responses directly within your browser or desktop environment, enabling faster, safer, and more flexible API testing without changing backend code.
Key capabilities of Requestly include:
- Intercept and Modify Requests: Capture outgoing API requests and incoming responses. Modify headers, body, or query parameters on the fly to test edge cases, debug issues, or simulate different scenarios without altering the backend.
- API Mocking and Response Simulation: Create mock endpoints with custom response bodies, HTTP status codes, and optional latency. This allows frontend development and testing to continue even if backend services are incomplete or unavailable.
- Support for Multiple Content Types: Work with JSON, XML, form data, or binary payloads. This versatility ensures comprehensive testing across diverse API formats.
- Pre/Post Request Scripting: Execute scripts before or after sending requests to set variables, modify headers, or validate responses, enabling more advanced and dynamic testing scenarios.
- Team Workspaces and Collaboration: Share configurations, mocks, and test scripts across teams. Workspaces ensure consistency and allow multiple developers to collaborate efficiently on API testing projects.
- Cross-Platform Compatibility: Use Requestly in a browser extension for quick testing or the desktop app for more comprehensive tasks across web, mobile, or desktop applications.
Conclusion
APIs enable systems to exchange data, extend functionality, and automate processes. They allow applications to access specific data or actions from other systems without exposing internal logic. Proper planning, request validation, and error handling, measures such as authentication, authorization, and encryption ensure API integrations work reliably.
Requestly helps developers test and debug APIs by intercepting, modifying, and mocking requests and responses. It allows teams to simulate different scenarios, verify endpoints, and catch issues before deployment without altering backend systems.

Contents
- What is an API?
- Benefits of Using APIs
- Different Types of APIs
- 1. Web APIs
- 2. RESTful APIs
- 3. SOAP APIs
- 4. GraphQL APIs
- 5. Public APIs
- How APIs Facilitate Communication Between Systems
- Key Protocols and Formats in API Communication
- Effective Strategies for API Integration
- Why API Security Matters
- Why Use Requestly for API Testing
- Conclusion
Subscribe for latest updates
Share this article
Related posts