X-Content-Type-Options: Benefits, Purpose, and Best Practices

Web browsers use HTTP headers to determine how to handle content from servers. The X-Content-Type-Options header instructs browsers to follow the declared content type and prevents them from executing files incorrectly. Without it, malicious scripts disguised as safe files can expose websites to attacks like cross-site scripting (XSS).
Enforcing strict MIME type checking reduces the risk of content sniffing and strengthens website security. It ensures web applications behave as intended and sensitive data remains protected. Proper implementation helps maintain user trust and safeguard web content.
This article explains the benefits, purpose, implementation steps, and best practices for using the X-Content-Type-Options header effectively.
Understanding X-Content-Type-Options
The X-Content-Type-Options header is a security feature that tells browsers to strictly follow the MIME type declared by the server. By default, some browsers try to “sniff” the content type of a file, which can lead to executing malicious scripts disguised as safe files like images or text. Setting this header ensures the browser treats each file according to its intended type.
There are two main directives for this header, but only one is commonly used: nosniff. When X-Content-Type-Options: nosniff is set, the browser will not override the server-declared content type, preventing attacks that exploit MIME type confusion. This simple header is lightweight yet highly effective, making it a fundamental part of a secure HTTP response.
Key Benefits of X-Content-Type-Options for Web Security
The X-Content-Type-Options header strengthens web security by enforcing strict MIME type handling, which directly impacts how browsers interpret content.
- Blocks Content Sniffing Exploits: Without this header, browsers may detect and execute a file type incorrectly. For example, an attacker could upload a .txt file containing JavaScript. With nosniff enforced, the browser treats it as plain text, preventing execution.
- Mitigates Cross-Site Scripting (XSS): Scripts embedded in disguised file types cannot run, reducing the risk of attackers injecting malicious code into pages or forms.
- Prevents Mixed Content Execution: Sites serving both images and scripts risk accidental execution of unsafe resources. Enforcing the header ensures only correctly typed files are processed, protecting assets and sensitive data.
- Enforces Consistent Behavior Across Browsers: Different browsers implement content sniffing differently. X-Content-Type-Options standardizes handling, so developers can rely on predictable behavior during testing and deployment.
- Simplifies Security Audits and Testing: By limiting browser interpretation, testers can focus on verifying known content types, making security testing more precise and reproducible.
Purpose of X-Content-Type-Options
The primary purpose of the X-Content-Type-Options header is to enforce strict MIME type validation, preventing browsers from interpreting files in unintended ways. Web applications often serve multiple content types, including HTML, JavaScript, JSON, and images. Without strict enforcement, a browser may “sniff” a file and execute it incorrectly, creating security gaps.
For example, a file uploaded as a .txt document could contain malicious JavaScript. If the browser misinterprets it as executable code, an attacker could inject scripts that steal session data, manipulate the DOM, or redirect users.
By setting X-Content-Type-Options: nosniff, developers ensure that the browser only executes content according to its declared type, eliminating this attack vector.
This header also complements other security measures, such as Content-Security-Policy and Strict-Transport-Security, forming a layered approach that enforces proper content handling and reduces overall vulnerability exposure.
How X-Content-Type-Options Protects Your Site from Vulnerabilities
The X-Content-Type-Options header protects websites by preventing browsers from misinterpreting files and executing unintended content. This reduces common web attack vectors and enforces predictable content handling.
- Prevents Execution of Malicious Scripts: Files uploaded as text or images cannot be executed as scripts. For example, a .jpg file containing embedded JavaScript cannot run if nosniff is enabled.
- Blocks MIME Type Confusion Attacks: Attackers often exploit browsers that automatically guess content types. Enforcing the header ensures that only correctly typed content is processed.
- Reduces XSS and Code Injection Risks: Malicious code embedded in incorrectly typed resources cannot execute, protecting user sessions and sensitive data.
- Secures Third-Party Content: Scripts or assets loaded from external sources are handled according to their declared type, reducing the risk of executing untrusted code.
- Supports Security Testing: Testers can reliably verify content types without unexpected browser behavior interfering, making vulnerability scans and automated tests more accurate.
Step-by-Step Guide to Implementing X-Content-Type-Options
To enforce the X-Content-Type-Options header, you need to configure your web server to instruct browsers to strictly follow declared content types. This guide provides practical steps for developers and testers to implement and verify the header effectively.
Step 1: Determine Your Server Environment: Identify which server your site uses, such as Apache, Nginx, or IIS, since the configuration method differs for each.
Step 2: Access Server Configuration Files: Open the server’s configuration file:
- Apache: httpd.conf or .htaccess
- Nginx: nginx.conf
- IIS: Web.config
Step 3: Add the X-Content-Type-Options Header: Insert the header with the nosniff directive to enforce strict MIME type handling:
1. Apache:
Header set X-Content-Type-Options "nosniff"2. Nginx:
add_header X-Content-Type-Options "nosniff";3. IIS:
<httpProtocol>
<customHeaders>
<add name="X-Content-Type-Options" value="nosniff" />
</customHeaders>
</httpProtocol>Step 4: Apply Changes: Save the configuration and restart or reload the server to activate the header.
Step 5: Verify Implementation: Check that the header is active using browser developer tools or curl:
curl -I https://yourwebsite.com
Look for X-Content-Type-Options: nosniff in the response headers.
Step 6: Test Across File Types: Serve different content types such as JavaScript, HTML, JSON, and images. Confirm the browser enforces the declared MIME types and does not execute any misinterpreted content.
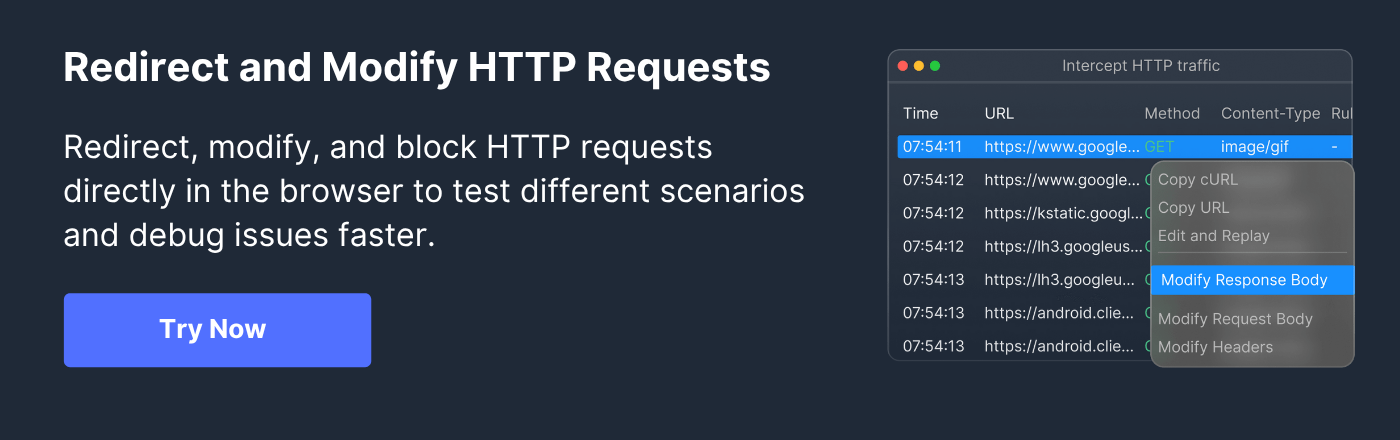
How Requestly Helps Optimize and Test X-Content-Type-Options
Testing and validating X-Content-Type-Options ensures your site handles content safely and consistently. Using Requestly, testers can intercept HTTP responses and inspect headers in real time to confirm the header is present and correctly configured.
- Intercept Responses: Capture server responses to check if X-Content-Type-Options: nosniff is included for all content types.
- Modify Headers for Testing: Simulate scenarios by adding, removing, or altering headers to see how the site behaves without strict MIME enforcement.
- Verify Browser Enforcement: Load different file types while Requestly monitors headers to ensure browsers follow the declared MIME types and do not execute misinterpreted content.
- Automate Repeated Checks: Set up rules in Requestly to repeatedly validate headers across pages and file types during development or staging, saving manual testing time.
Troubleshooting X-Content-Type-Options Configuration Issues
While implementing X-Content-Type-Options is straightforward, teams often face issues when it fails to appear consistently across responses or behaves unpredictably during testing.
Here are the most common X-Content-Type-Options configuration issues and how to solve them.
1. Header Missing in Response A missing header usually indicates a configuration or scope issue. Incomplete directives or incorrect placement within the server file can cause browsers to ignore the setting entirely.
- Check for syntax errors or missing quotation marks in the configuration.
- Verify that the header is defined in the correct block (server, location, or http for Nginx; global or directory-level for Apache).
- After updating the configuration, restart or reload the server to ensure the change is applied.
2. Header Overridden by Proxy or CDN In modern setups, reverse proxies or CDNs often sit between your origin server and the client. These intermediaries can strip or override security headers if not configured properly.
- Review your proxy rules to ensure headers from the origin are preserved.
- In CDNs like Cloudflare or AWS CloudFront, explicitly set rules that forward or append X-Content-Type-Options to all cached assets.
- Run tests both through and bypassing the CDN to confirm consistency.
3. Header Applied to Limited File Types Sometimes the header appears for HTML pages but not for scripts, JSON, or images. This happens when the configuration only applies to certain MIME types or directories.
- Update the rule to include all responses, not just web pages.
- Confirm that static assets, API responses, and third-party scripts also carry the header.
- Apply it globally at the server or framework level to avoid missing resources.
4. Mixed Responses with Conflicting Headers In multi-service environments, inconsistent configurations can lead to conflicts where some services send the header while others don’t. This weakens protection and complicates debugging.
- Standardize header settings across all services sharing a domain or subdomain.
- Use middleware in frameworks or reverse proxies to inject the header uniformly.
- For containerized or microservice architectures, include the directive in each service’s base image or API gateway.
5. Testing Tools Showing Inconsistent Results Apparent inconsistencies may not be misconfigurations but caching artifacts. Cached responses may lack recently added headers, leading to false negatives in validation.
- Clear the browser cache or disable caching while testing.
- Use Requestly to inspect live headers directly from the origin server.
- Repeat the test across different browsers to confirm consistent enforcement.
Best Practices for Using X-Content-Type-Options
Once the header is implemented correctly, the focus should shift to maintaining consistency, integrating it into testing processes, and ensuring that it scales with deployment changes.
The following best practices help teams manage X-Content-Type-Options effectively beyond initial setup.
- Automate Header Validation: Include header checks in deployment or testing workflows to ensure nosniff is consistently applied across environments.
- Use Layered Security: Combine X-Content-Type-Options with headers like Content-Security-Policy, Referrer-Policy, and Strict-Transport-Security for complete protection.
- Audit External Resources: Periodically review third-party scripts, APIs, and assets to ensure they do not bypass MIME restrictions or weaken enforcement.
- Centralize Configuration: Apply the header globally through framework middleware or server templates so all routes and content types remain covered.
- Revalidate After Infrastructure Changes: Recheck headers after CDN, proxy, or load balancer updates to confirm policies persist across all delivery paths.
- Maintain Clear Documentation: Keep internal notes on why and how the header is configured to support audits, onboarding, and consistent implementation.
Conclusion
The X-Content-Type-Options header is a small but powerful control that strengthens web security by enforcing strict MIME type validation. It helps prevent content sniffing, reduces the risk of script execution attacks, and ensures browsers handle files as intended.
With Requestly, testers and developers can intercept, modify, and verify HTTP responses in real time to confirm that headers like X-Content-Type-Options are configured correctly. This helps ensure consistent security behavior across environments and simplifies validation during testing and deployment.

Contents
- Understanding X-Content-Type-Options
- Key Benefits of X-Content-Type-Options for Web Security
- Purpose of X-Content-Type-Options
- How X-Content-Type-Options Protects Your Site from Vulnerabilities
- Step-by-Step Guide to Implementing X-Content-Type-Options
- How Requestly Helps Optimize and Test X-Content-Type-Options
- Troubleshooting X-Content-Type-Options Configuration Issues
- Best Practices for Using X-Content-Type-Options
- Conclusion
Subscribe for latest updates
Share this article
Related posts