What is X-Forwarded-For: A Complete Guide


The X-Forwarded-For header is a standard HTTP header used to identify the original client IP address when a request passes through proxies or load balancers. Many web applications rely on this header to accurately track client activity, enforce security policies, and manage traffic routing.
In modern web architectures, requests often traverse multiple intermediaries, including reverse proxies, content delivery networks, and firewalls. Without X-Forwarded-For, the server only sees the IP of the last proxy, which can complicate logging, analytics, and security enforcement. Proper handling of this header ensures that applications can correctly identify and respond to client requests.
This article explains how X-Forwarded-For works, its impact on web applications, common challenges, best practices, and testing approaches using Requestly for accurate client IP handling.
What Is X-Forwarded-For and Why Does It Matter?
The X-Forwarded-For (XFF) header is an HTTP header that conveys the original client IP address when a request passes through one or more proxies or load balancers. It is typically added by the first proxy in the chain and can contain multiple IP addresses if the request traverses multiple intermediaries, separated by commas.
Here are some key reasons X-Forwarded-For is essential:
- Accurate Client Identification: Without XFF, servers see only the IP of the last proxy, not the actual client. For example, in an analytics system, relying solely on the proxy IP would misrepresent user location and behavior.
- Security Enforcement: Firewalls, rate limiting, and access controls often need the original client IP. Using XFF ensures these rules apply correctly, even behind proxies.
- Audit and Logging: For compliance or incident investigation, logs need to reflect the true source of requests. XFF provides visibility into request origin that would otherwise be masked.
- Geo-Targeting and Personalization: Applications that serve location-specific content can use XFF to determine the client’s true geographic location, avoiding proxy-based inaccuracies.
- Troubleshooting and Performance Monitoring: Identifying the real client IP helps trace errors, detect abusive patterns, and measure latency accurately, improving monitoring and diagnostics.
In short, X-Forwarded-For acts as a bridge between client requests and server visibility, enabling accurate tracking, security, and auditing in complex web environments.
How X-Forwarded-For Impacts Web Application Architecture
Since many modern applications operate behind reverse proxies, load balancers, or content delivery networks (CDNs), the server cannot rely on the source IP alone. Incorporating XFF into the architecture ensures that client-related decisions are based on accurate information.
Key impacts of XFF on application architecture include:
- Request Routing and Load Balancing: Applications that perform IP-based routing or session persistence require the original client IP. XFF allows the load balancer or application logic to direct traffic correctly even when multiple proxies are involved.
- Security Layer Placement: Firewalls, API gateways, and WAFs often need to inspect client IPs for filtering or rate limiting. Architectures must be designed to read XFF before applying rules to prevent bypasses caused by intermediate proxies.
- Logging and Monitoring Infrastructure: Logging frameworks and analytics pipelines must parse XFF to store the true client IP. Without this, monitoring data may reflect proxy IPs, skewing metrics and hiding patterns of malicious traffic.
- Application-Level Policies: Rate limiting, access control, and geo-targeted content delivery rely on accurate client identification. Using XFF ensures these policies are enforced consistently across distributed systems.
- Microservices and Distributed Systems: In architectures with multiple microservices, propagating XFF through service-to-service calls preserves client context, which is crucial for auditing, security, and debugging.
The Role of X-Forwarded-For in Identifying Client IP
The X-Forwarded-For header plays a central role in determining the actual client IP when requests pass through one or more proxies. Without it, the server sees only the last proxy’s IP, which can obscure the origin of requests and impact security, logging, and analytics.
Key aspects of XFF in identifying client IP include:
- Single Proxy Scenarios: When a request passes through one proxy, XFF contains a single IP address representing the client. This allows the server to log the true origin and enforce IP-based security rules. For example, a rate-limiting module can block a specific client IP instead of mistakenly blocking the proxy.
- Multiple Proxy Chains: In environments with multiple intermediaries, XFF stores a comma-separated list of IPs. The first IP typically represents the original client, while subsequent IPs indicate each proxy in the chain. Understanding this order is crucial for accurate client identification.
- Trust Boundaries: Applications must determine which proxies are trusted to set XFF correctly. Accepting XFF from untrusted sources can allow IP spoofing, where an attacker forges a false client IP. By validating trusted proxies, servers can reliably extract the client IP.
- Security and Access Control: Accurate client IP identification enables proper enforcement of firewall rules, geolocation restrictions, and blacklisting. For example, only allowing traffic from specific regions or blocking repeated malicious requests depends on reading the correct IP from XFF.
- Integration with Logging and Analytics: Web servers, load balancers, and analytics tools can store the true client IP from XFF, ensuring accurate tracking of user behavior, traffic patterns, and debugging data.
How X-Forwarded-For Affects Logging and Analytics
When requests pass through proxies or load balancers, relying on the source IP alone can lead to inaccurate data. X-Forwarded-For ensures logs and analytics reflect the true origin of client requests, which is essential for security audits, performance monitoring, and user behavior analysis.
Key considerations for logging and analytics include:
- Accurate Client Tracking: By using the first IP in the XFF list, servers and analytics tools can identify the real client rather than just the last proxy. For example, web traffic analysis can correctly determine user locations and session behavior.
- Security Auditing: Logs that include XFF provide a clear chain of request origin. This helps trace malicious activity, detect repeated attacks, and comply with regulatory requirements that mandate source identification.
- Performance Monitoring: Latency, request frequency, and error rates can be correlated with real client IPs to identify bottlenecks or abusive clients. Without XFF, metrics may incorrectly attribute issues to intermediate proxies.
- Data Aggregation and Reporting: Analytics dashboards rely on accurate IP data to generate reports. Incorporating XFF avoids misleading patterns caused by proxy clustering, ensuring insights into actual user distribution and traffic trends.
- Anomaly Detection: Identifying unusual traffic patterns, such as sudden spikes from a single client, requires the true client IP. Using XFF prevents proxy IPs from masking suspicious behavior.
X-Forwarded-For in a Load-Balanced Environment: Key Considerations
In load-balanced environments, multiple servers handle incoming requests, often through one or more proxies. Proper handling of the X-Forwarded-For (XFF) header is critical to ensure accurate client identification, consistent session management, and effective security enforcement across all nodes.
Key considerations include:
- Preserving the Original Client IP: Each load balancer or proxy must append its own IP to the XFF header rather than overwriting it. This ensures that the first IP in the chain always represents the actual client. For example, in a multi-tiered system with two load balancers, the XFF might look like 203.0.113.5, 198.51.100.10.
- Session Affinity (Sticky Sessions): Many applications use client IPs to maintain session persistence. Using the correct IP from XFF ensures that the same client consistently reaches the same backend server when session affinity is required.
- Security Filtering Across Nodes: Firewalls, WAFs, and rate limiters at each node must reference the client IP from XFF, not the proxy IP. Misconfiguration can allow bypasses, as untrusted traffic may appear as originating from internal infrastructure.
- Logging Consistency: Centralized logging systems must extract the client IP from XFF to maintain accurate logs across multiple servers. Without this, distributed logs could misrepresent client activity and make debugging more difficult.
- Handling Multiple Proxies: In complex networks with CDN or reverse proxy layers, each node may append its IP. Applications must parse the XFF header correctly and trust only verified proxies to avoid spoofing attacks.
Diagnosing and Resolving Common Issues with X-Forwarded-For
Even with proper configuration, issues with the X-Forwarded-For header can arise, affecting client identification, security, and logging. Understanding common problems and how to resolve them is crucial for maintaining reliable web application behavior.
1. Incorrect Client IP in Logs
In many environments, logs and analytics display the wrong client IP because proxies overwrite the XFF header or applications extract the wrong IP from the chain. This misidentification can affect security enforcement, session routing, and traffic analysis, making it difficult to trace user activity accurately.
To address this, configure all proxies and load balancers to append their IPs instead of overwriting the header. Ensure backend servers consistently extract the first IP in the XFF chain as the original client, and regularly audit logging and analytics systems to verify accurate tracking, geolocation, and security enforcement.
2. IP Spoofing
Attackers or untrusted intermediaries can inject fake IP addresses into the XFF header, potentially bypassing rate limiting, firewall rules, or access controls. This can create serious security vulnerabilities and obscure malicious activity.
Mitigation involves accepting XFF values only from trusted proxies and implementing validation for all incoming headers. Malformed or suspicious IPs should be rejected, and security rules should operate on verified client IPs rather than trusting the header blindly.
3. Session Affinity Failures
In load-balanced environments, session persistence can break if the system relies on the last proxy IP instead of the original client IP. This can cause users to be routed inconsistently across backend servers, disrupting session-dependent features and creating a poor user experience.
To prevent this, ensure load balancers and routing mechanisms use the first IP from the XFF chain for session persistence. Consistent handling of XFF across all nodes is essential for maintaining reliable routing and accurate client identification.
4. Skewed Analytics Data
Ignoring the XFF header or misconfiguring analytics pipelines can result in traffic metrics, geolocation, and user behavior data being tied to proxy IPs rather than the actual clients. This produces inaccurate insights and affects decision-making based on traffic trends.
Correcting this requires updating logging and analytics systems to parse the first IP from XFF. Recording both the full XFF chain and the extracted client IP ensures precise tracking, accurate reporting, and reliable performance monitoring.
Best Practices for Securing and Configuring X-Forwarded-For
Proper configuration and handling of the X-Forwarded-For header is critical to prevent security risks, ensure accurate client identification, and maintain reliable logging and analytics. Implementing best practices minimizes the risk of spoofed IPs and operational issues in complex network environments.
1. Trust Only Verified Proxies
The XFF header can be manipulated by clients or untrusted intermediaries. Only accept XFF values from known and trusted proxies or load balancers. Applications should validate the IP chain and ignore headers from unverified sources.
2. Preserve the Full XFF Chain
Each proxy should append its IP to the existing XFF header rather than overwriting it. This preserves the complete request path, allowing backend servers to extract the true client IP while maintaining visibility into intermediate nodes.
3. Extract the Correct Client IP
When processing XFF, always use the first IP in the chain as the original client. Ensure that your security rules, logging systems, and analytics pipelines rely on this IP to prevent misidentification.
4. Implement IP Validation and Filtering
Verify that the extracted IP is a valid public or private address and apply filtering rules accordingly. Reject malformed or suspicious IPs to prevent injection or spoofing attacks.
5. Centralize Logging and Monitoring
Record both the full XFF chain and the extracted client IP in logs. Centralized logging ensures consistent monitoring, aids troubleshooting, and provides accurate analytics for traffic patterns, geolocation, and security audits.
6. Keep Configurations Consistent Across Environments
Ensure that XFF handling is uniform across all servers, proxies, and load balancers. Inconsistent configurations can lead to incorrect IP detection, broken session affinity, or misapplied security policies.
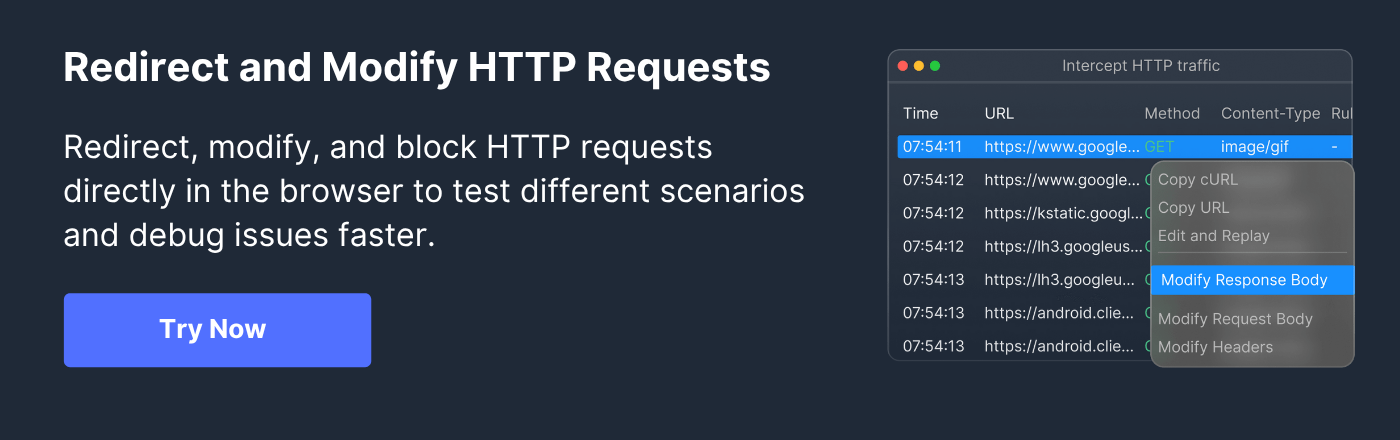
How to Use Requestly to Test X-Forwarded-For
Requestly is a browser-based HTTP interception and modification tool that enables testers and developers to manipulate web requests in real time. It allows you to inspect headers, modify requests, and simulate different network conditions without changing the server configuration.
For testing X-Forwarded-For, Requestly helps validate how applications interpret client IPs, check session routing, and verify security rules when requests pass through proxies or load balancers. You can simulate multiple client IPs and observe how the server processes them.
Here are the core features of Requestly that help test X-Forwarded-For:
- Intercept Requests: Capture and view outgoing requests to inspect existing XFF headers and their values.
- Modify Headers: Add or change XFF values to simulate requests from different client IPs.
- Validate Security Rules: Test rate limiting, firewall, and access control policies using custom XFF values.
- Check Session Affinity: Test how backend routing and session persistence respond to varying client IPs.
- Monitor Logs and Responses: Confirm that the server correctly logs the original client IP and returns expected responses.
Alternatives to X-Forwarded-For in Web Security
While X-Forwarded-For is widely used to identify client IPs, it has limitations, including vulnerability to spoofing and reliance on trusted proxies. Web applications can adopt alternative methods or complementary approaches to enhance security and ensure accurate client identification.
1. Proxy Protocol
The Proxy Protocol is a standardized way for load balancers and proxies to transmit client connection information, including IP and port, to backend servers. Unlike XFF, it is transmitted at the transport layer, reducing the risk of header tampering. Implementing the Proxy Protocol allows servers to reliably extract client details without relying solely on HTTP headers.
2. True-Client-IP Header
Some CDNs, like Akamai and Cloudflare, provide a True-Client-IP header to indicate the original client IP. This header is typically added by the CDN and trusted by the origin server. Using True-Client-IP helps avoid ambiguity when multiple proxies append XFF values.
3. Mutual TLS (mTLS)
Mutual TLS can authenticate clients directly at the transport layer, providing strong assurance of client identity. While not a direct replacement for XFF, it complements IP-based identification by cryptographically verifying the client, reducing the reliance on headers that can be spoofed.
4. IP Reputation Services
Services that maintain databases of known malicious IPs or proxy networks can supplement XFF validation. Applications can cross-check the extracted IP against these services to block or flag suspicious traffic, adding a layer of security beyond header inspection.
5. Network-Level Logging
Instead of relying solely on HTTP headers, network devices like firewalls or load balancers can log client connection information at the transport layer. These logs provide a trusted record of client IPs that is less susceptible to manipulation.
Conclusion
The X-Forwarded-For header is essential for identifying client IPs in environments with proxies, load balancers, or CDNs. Proper handling ensures accurate logging, session routing, security enforcement, and analytics, while misconfigurations can lead to spoofed IPs, broken sessions, or skewed traffic metrics.
Testing and validating XFF using Requestly helps verify that applications process client IPs correctly under different scenarios. By intercepting requests, modifying headers, and simulating multiple client IPs, testers can confirm that logging, security rules, session management, and analytics behave as expected, ensuring robust and accurate client identification across the application stack.

Contents
- What Is X-Forwarded-For and Why Does It Matter?
- How X-Forwarded-For Impacts Web Application Architecture
- The Role of X-Forwarded-For in Identifying Client IP
- How X-Forwarded-For Affects Logging and Analytics
- X-Forwarded-For in a Load-Balanced Environment: Key Considerations
- Diagnosing and Resolving Common Issues with X-Forwarded-For
- Best Practices for Securing and Configuring X-Forwarded-For
- How to Use Requestly to Test X-Forwarded-For
- Alternatives to X-Forwarded-For in Web Security
- Conclusion
Subscribe for latest updates
Share this article
Related posts