Learn about Accept-Encoding in HTTP Requests
Your lightweight Client for API debugging
No Login Required
Requestly is a web proxy that requires a desktop and desktop browser.
Enter your email below to receive the download link. Give it a try next time you’re on your PC!










Efficient data transfer is at the core of web performance. The HTTP protocol employs various headers that shape how information moves between clients and servers.
One such header, Accept-Encoding, plays a crucial role in negotiating the format and compression of web resources, affecting everything from page speed to bandwidth cost.
Definition of Accept-Encoding
The Accept-Encoding HTTP header is used by a client (such as a browser or API consumer) to inform the server about the compression algorithms it can handle. By listing supported encodings, the client enables the server to respond with optimally compressed data, reducing transfer sizes without altering the underlying content.
How Accept-Encoding Works
When a client sends a request, it appends the Accept-Encoding header, indicating which compression methods—like gzip, deflate, or Brotli—it understands. The server examines these options and chooses one it supports.
The selected encoding is then applied, and the server adds a Content-Encoding header to the response to inform the client how to decompress the data.
Example:
GET /index.html HTTP/1.1
Host: www.example.com
Accept-Encoding: gzip, deflate, br
If the server selects gzip:
text
Content-Encoding: gzipThe client then decompresses the content accordingly.
Importance of Accept-Encoding in HTTP
The ability to negotiate content encoding is vital for optimizing web performance. Compression reduces the size of data transmitted, lowering bandwidth usage, accelerating load times, and providing a smoother user experience.
Especially for resource-heavy websites, efficient encoding translates into significant cost and speed benefits.
Supported Content-Encoding Algorithms
Modern web servers and clients support a range of encoding algorithms. Here’s an overview:
- gzip: Utilizes the LZ77 compression algorithm with CRC-32. Widely adopted for text-based resources due to compatibility and speed.
- deflate: Uses zlib structure and the DEFLATE algorithm. Similar to gzip but results may vary.
- br (Brotli): Offers superior compression ratios for many assets, especially text. Commonly used by high-performance sites.
- compress: Older LZW-based method, now mostly deprecated.
- identity: No transformation—the data is sent as-is.
- * (wildcard): Accepts any encoding available.
Brotli, gzip, and deflate dominate today’s landscape due to their robust support and efficiency.
Syntax and Directives of Accept-Encoding
The Accept-Encoding header follows a simple syntax but supports advanced directives:
Accept-Encoding: gzip, deflate, br
Accept-Encoding: br;q=1.0, gzip;q=0.8, *;q=0.1
Directives like q-values communicate preferences (explained below), and identity or wildcard $$*) can be used for broader negotiation.
Client Preferences and Quality Values (q-values)
Clients can specify preferred encodings with q-values—decimals from 0 (lowest) to 1 (highest):
text
Accept-Encoding: br;q=1.0, gzip;q=0.8, *;q=0.1Here, the client prefers Brotli most, then gzip, then any other method. Q-values empower fine-grained negotiation and minimize failed content exchanges.
- If multiple encodings share the same q-value, the most specific is chosen.
- If identity;q=0 is specified, “no encoding” is forbidden.
Accept-Encoding in HTTP Requests and Responses
Requests: The client sends Accept-Encoding to propose what it can accept. Responses: The server selects from the proposals, compresses the data, and signals its choice via Content-Encoding. If none of the requested encodings are supported, a 406 Not Acceptable status may be returned.
Browser and Client Support for Accept-Encoding
Major browsers—Chrome, Firefox, Safari, Edge, Opera—support gzip, deflate, and increasingly Brotli. API clients and tools (like curl) can explicitly set the header.
- Modern browsers automatically manage Accept-Encoding; developers seldom need to manually configure it.
- Brotli’s support exceeds 95% globally, making it viable for most web audiences.
Impact on Web Performance and Bandwidth
Optimal use of Accept-Encoding delivers several benefits:
- Reduces Data Transfer: Compresses resources, shrinking file sizes—critical for mobile and slow networks.
- Speeds Page Loads: Smaller assets mean faster rendering and interaction.
- Lowers Hosting Costs: Significant savings for high-traffic sites.
- Enhances SEO: Search engines favor fast sites.
Sites not leveraging content compression miss out on substantial performance gains, particularly for text-heavy content.
Common Issues and Troubleshooting
While powerful, Accept-Encoding can cause issues:
- 406 Not Acceptable errors: When the server can’t honor any proposed encoding due to misconfiguration or unsupported methods.
- Double Compression: Recompressing already compressed files increases size and may corrupt data.
- Browser Quirks: Some browsers handle the header differently, which may cause inconsistencies.
- Vary Header Problems: Failing to send the correct Vary: Accept-Encoding header can lead to caching issues, serving the wrong content to users.
Troubleshooting steps include examining headers in browser dev tools, adjusting server configuration, and validating with diagnostic utilities.
Best Practices for Implementing Accept-Encoding
To maximize web performance and compatibility:
- Always use gzip or Brotli for text-based resources; fallback to deflate as needed.
- Ensure your server is properly configured to detect clients’ Accept-Encoding proposals.
- Set the Vary: Accept-Encoding header to avoid problematic caching and CDN mismatches.
- Avoid compressing binary formats (JPEG, MP4) that are already compressed.
- Monitor computational resource usage—disable compression at high CPU load if necessary.
Tools for Inspecting and Debugging Accept-Encoding
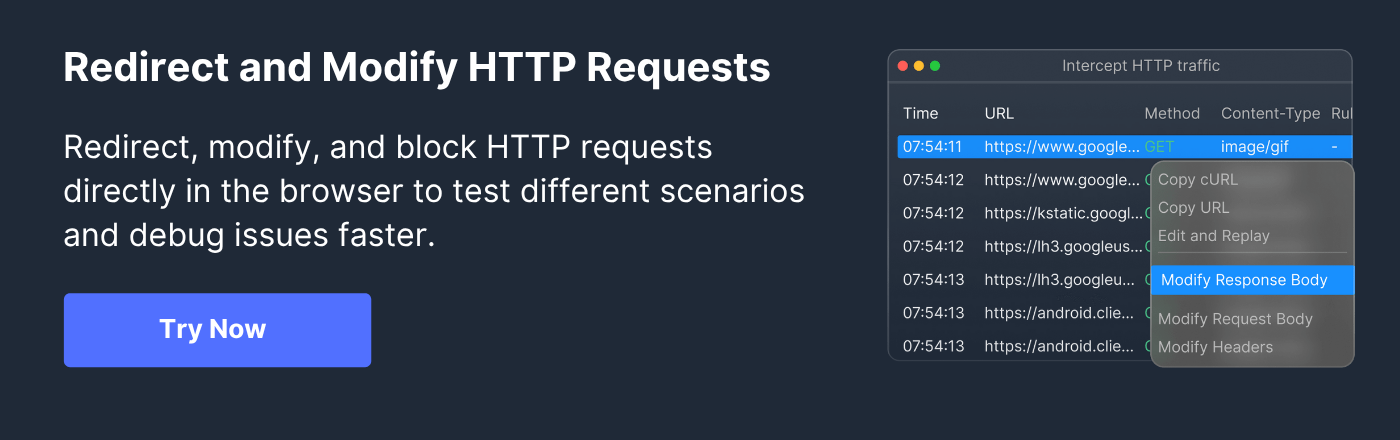
Debugging Accept-Encoding requires visibility into request and response headers. Modern browsers offer built-in network inspection, and command-line tools like curl and Postman allow explicit header manipulation. For advanced scenarios, interception platforms can modify, simulate, or test encoding behavior.
Using Requestly HTTP Interceptor Tool
To facilitate custom Accept-Encoding header experimentation, the Requestly HTTP Interceptor
provides granular control over HTTP headers. With Requestly, developers can:
- Modify or inject Accept-Encoding headers in real time to observe server responses.
- Debug scenarios where compression negotiation fails or needs fine-tuning.
- Automate testing of q-value preferences and complex content negotiation workflows.
Requestly is highly effective when troubleshooting compatibility, CDN variation, or bespoke API behaviors that rely on specific encoding strategies.
Security Considerations
Content encoding interacts subtly with web security. If compression algorithms are misused (e.g., compressing sensitive or pre-compressed data), it can inadvertently expose vulnerabilities like BREACH and CRIME attacks on HTTPS traffic. Avoid compressing data that contains secrets alongside attacker-controlled content, and keep libraries updated to mitigate known exploits.
Additionally, mismatches in encoding or charset handling can allow attackers to inject malicious payloads if encoding or decoding steps are misaligned.
Conclusion
Accept-Encoding is a linchpin of efficient and secure web data delivery. Proper understanding and implementation enable dramatic gains in speed, resource savings, and user satisfaction.
By leveraging modern encodings, configuring servers thoughtfully, and employing debugging tools such as Requestly, developers ensure their web services operate at peak potential while safeguarding users from potential risks.
Contents
- Definition of Accept-Encoding
- How Accept-Encoding Works
- Importance of Accept-Encoding in HTTP
- Supported Content-Encoding Algorithms
- Syntax and Directives of Accept-Encoding
- Client Preferences and Quality Values (q-values)
- Accept-Encoding in HTTP Requests and Responses
- Browser and Client Support for Accept-Encoding
- Impact on Web Performance and Bandwidth
- Common Issues and Troubleshooting
- Best Practices for Implementing Accept-Encoding
- Tools for Inspecting and Debugging Accept-Encoding
- Using Requestly HTTP Interceptor Tool
- Security Considerations
- Conclusion
Subscribe for latest updates
Share this article
Related posts
Get started today
Requestly is a web proxy that requires a desktop and desktop browser.
Enter your email below to receive the download link. Give it a try next time you’re on your PC!