Understanding the GET Method: Features, Usage, and Best Practices


The GET method is a fundamental part of the HTTP protocol, enabling efficient and straightforward data retrieval from servers. Its simplicity and cache-friendly nature make it ideal for many web applications, but awareness of its limitations and security considerations is crucial.
By understanding how GET works and applying best practices, developers can use it effectively in their projects.
Understanding GET Method
The GET method is one of the most commonly used HTTP request methods in web communication. It is primarily designed to retrieve data from a server without causing any side effects or changes on the server’s resources.
When a client, such as a web browser, sends a GET request, it asks the server to return the specified resource, like a webpage, image, or data in a particular format.
One of the key characteristics of the GET method is that all data sent to the server is appended to the URL as query parameters, making the request visible and easily shareable.
Because of its idempotent nature, multiple identical GET requests will have the same effect as a single request, meaning it does not alter the server state. This behavior aligns with GET’s intended use for safe and repeatable data retrieval operations.
Understanding the GET method is foundational for web developers and API consumers, as it forms the basis for most data-fetching activities on the internet. Its use helps ensure efficient, clear, and stateless client-server communication.
Key Features of GET Method
The GET method has several key features that make it essential for web communication:
- Data Retrieval Focused: GET is designed specifically to request data from a server without modifying any resources, ensuring safe and read-only operations.
- URL-Based Parameters: All data sent with a GET request is appended to the URL as query strings, making the parameters visible and easy to bookmark or share.
- Idempotent and Safe: Repeating the same GET request multiple times produces the same result without side effects on the server, which ensures reliable and predictable behavior.
- Cacheable: Responses to GET requests can often be cached by browsers and intermediate caches, improving performance and reducing server load.
- Limited Data Length: Due to URL length restrictions in browsers and servers, GET requests are suitable for sending small amounts of data only.
- Simple to Debug: Since all information is visible in the URL, GET requests are straightforward to log, inspect, and debug.
These features collectively make the GET method ideal for retrieving public or user-requested data efficiently and safely.
How GET Method Works
The GET method operates as a straightforward way for a client to request data from a server by specifying a URL. Here is a step-by-step overview of how the GET method works:
- Client Sends Request: The client, such as a web browser or API consumer, sends a GET request to the server. Any data needed to specify the request is included in the URL as query parameters, formatted as key-value pairs (e.g., ?key1=value1&key2=value2).
- Server Receives and Processes Request: The server receives the GET request and examines the URL and query parameters to determine which resource or data is being requested.
- Server Retrieves Data: The server locates the appropriate resource or generates the requested data based on the URL and parameters.
- Server Sends Response: The requested data is sent back to the client in the response body. This could be an HTML page, an image, JSON, or other types of data. The server also includes a status code indicating whether the request was successful.
- Stateless Nature: Each GET request is independent and stateless, meaning the server treats every request separately without relying on previous interactions.
- Visibility and Caching: Since all data in a GET request is part of the URL, it is visible to users, can be bookmarked, shared, logged, and cached by browsers and servers for faster retrieval.
This process makes the GET method efficient for retrieving data while keeping the interactions simple and transparent.
Best Practices and Limitations of GET Method
To ensure effective and secure use of the GET method, it is important to follow certain best practices while also being aware of its inherent limitations.
Best Practices
The best practices to use the GET method include:
- Use GET Only for Data Retrieval: GET requests should strictly be used to fetch data without causing any changes on the server. Avoid using GET for actions like updates or deletions to maintain safe and predictable operations.
- Keep URLs Short and Clean: Since all data in GET requests is included in the URL, keep URLs concise to avoid exceeding browser or server URL length limits (usually around 2048 characters).
- Avoid Sensitive Data in URLs: Do not send confidential information (e.g., passwords, credit card numbers) via GET, as URLs are visible in browser history, logs, and can be shared unintentionally.
- Enable Caching for Performance: Use appropriate cache-control headers to allow browsers and proxies to cache GET responses, improving load times for frequently requested resources.
- Bookmarkable and Shareable URLs: Because GET request data is in the URL, it is easy to bookmark or share links to specific query results or resources.
- Avoid Request Body in GET: Although technically possible, avoid sending a body with GET requests, as it is not widely supported or expected by servers and clients.
Limitations
The limitations include:
- URL Length Restriction: GET requests are limited by maximum URL length, which can restrict the amount of data sent. This makes GET unsuitable for transmitting large or complex data.
- Security Concerns: Because query parameters are visible in URLs, GET requests can expose sensitive data, potentially leading to security vulnerabilities.
- Not Suitable for State Changes: GET should never be used for operations that modify server state, as it violates HTTP semantics and can cause unintended consequences if repeated.
- Cache Invalidation Complexity: Caching can lead to stale data if not managed properly, requiring careful cache-control mechanisms when data updates frequently.
By following these best practices and understanding its limitations, developers can leverage the GET method effectively for safe and efficient data retrieval in web applications.
Example Walkthrough: HTTP GET
To better understand how the GET method works in practice, let’s walk through a simple HTTP GET request example:
GET /contact HTTP/1.1
Host: example.com
User-Agent: curl/8.6.0
Accept: */*
- Request Line: The first line specifies the GET method requesting the /contact resource using HTTP version 1.1.
- Host Header: Identifies the domain name of the server (example.com) to which the request is sent.
- User-Agent Header: Provides information about the client making the request, here showing curl as the client.
- Accept Header: Indicates that the client accepts any type of response content (*/*).
When the server receives this request, it responds with the requested resource if available, typically including:
- Status Line: An HTTP status code, such as 200 OK, indicating successful retrieval.
- Response Headers: Metadata about the response, like content type (text/html), length, and modification date.
- Response Body: The actual content of the requested resource, for example, an HTML webpage.
This example demonstrates how GET requests operate with clear, visible parameters encoded in the request line and headers, and no request body involved, maintaining simplicity and transparency in data retrieval.
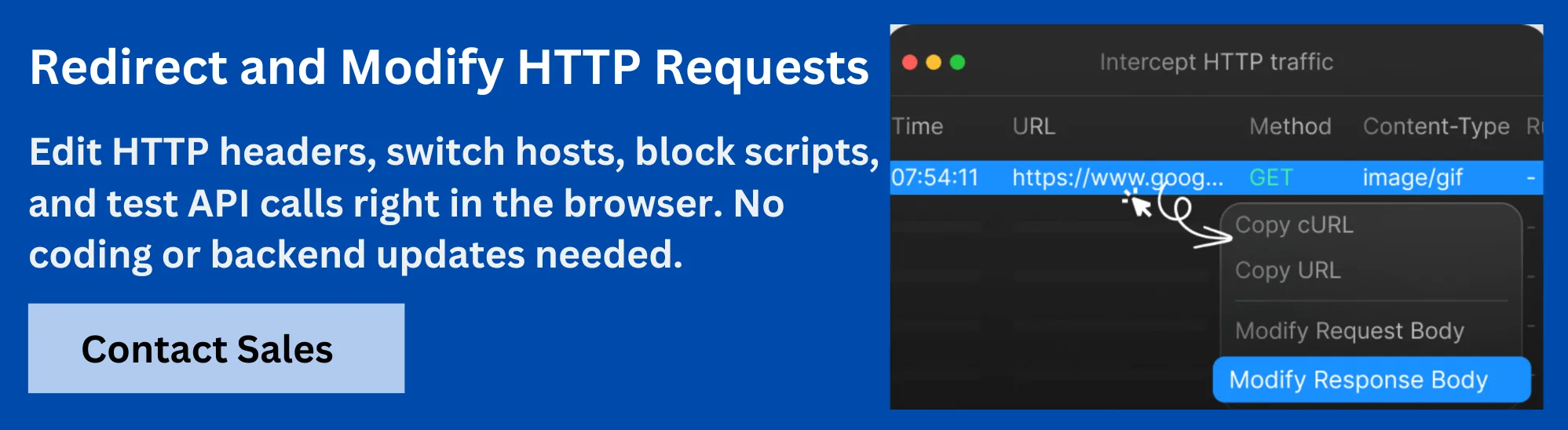
Debugging GET Requests with Requestly HTTP Interceptor
Debugging GET requests becomes much simpler and more efficient with tools like Requestly by BrowserStack. It offers an HTTP Interceptor, which allows developers to intercept, inspect, and modify HTTP requests and responses directly within their browser or development environment. This enables real-time monitoring and troubleshooting of the request lifecycle without changing the underlying code.
Key capabilities include:
- Intercepting Requests and Responses: Capture outgoing GET requests and incoming responses to analyze headers, parameters, status codes, and response bodies.
- Modifying Query Parameters and Headers: Change request URLs, query strings, or HTTP headers on the fly to test different scenarios or debug issues.
- Mocking Server Responses: Simulate various server responses to test frontend behavior without needing backend changes.
- Organizing and Sharing Rules: Create, save, and share interception and modification rules with team members for consistent debugging workflows.
Using Requestly, developers can quickly identify issues such as incorrect query parameters, missing headers, or unexpected server responses, improving the speed and quality of API development and testing. This makes it an essential tool for anyone working with HTTP GET requests in web applications.
Conclusion
The GET method remains a vital and widely used HTTP request type for retrieving data from servers in a safe, efficient, and predictable manner. Its characteristics of being idempotent and cacheable make it ideal for fetching resources without causing side effects.
However, understanding its limitations, such as URL length restrictions and sensitivity concerns, is crucial to using it appropriately.
By following best practices and leveraging tools like Requestly HTTP Interceptor for debugging, developers can maximize the effectiveness and security of GET requests in their web applications and APIs. Mastery of the GET method is foundational for building robust and reliable web communication.

Contents
Subscribe for latest updates
Share this article
Related posts