GET vs POST: Key Differences

Your lightweight Client for API debugging
No Login Required
Requestly is a web proxy that requires a desktop and desktop browser.
Enter your email below to receive the download link. Give it a try next time you’re on your PC!










Understanding the nuances between HTTP GET and POST methods is essential for anyone working with APIs or web development. These two request types serve distinct purposes in how data is transmitted and handled between clients and servers, influencing performance, security, and application behavior.
This article offers a comprehensive comparison of GET and POST, explaining their core differences, appropriate use cases, and practical considerations to help developers and testers make informed decisions when designing or testing APIs.
What Are GET and POST Methods?
GET and POST are two of the most common HTTP methods used in web communication.
Understanding their difference is crucial as each method aligns with different operational goals and security considerations.
GET Method
The GET method is primarily used to retrieve data from a specified resource on the server. When a client sends a GET request, it asks the server to return the requested data without making any changes to the resource. The parameters for a GET request are appended to the URL in the form of a query string.
GET requests are considered safe because they do not modify server data, and they are also idempotent, meaning multiple identical GET requests have the same effect as a single request.
Additionally, GET requests are cacheable, can be bookmarked, and remain in browser history, making them suitable for retrieving non-sensitive information like web pages, images, or JSON data.
POST Method
In contrast, the POST method is designed to send data to the server to create or update resources. The data sent in a POST request is included in the request body, allowing for larger, more complex data than GET requests.
Unlike GET, POST is not considered safe or idempotent because it can change the server state or cause side effects, such as submitting form data or uploading a file. POST requests are neither cached nor bookmarked, and their data does not appear in the URL, making them a better choice for transmitting sensitive information.
GET vs POST: Key Differences
Here is a comparison table showing the key differences between GET and POST methods:
Aspect | GET | POST |
Data Location | Sent as URL query parameters | Sent in the HTTP request body |
Data Size Limit | Limited (URL length restrictions, ~2048 chars) | No significant size limitation |
Security | Less secure (data visible in URL and browser history) | More secure (data not visible in URL or history) |
Caching | Can be cached | Not cached |
Bookmarking | Can be bookmarked | Cannot be bookmarked |
Data Type Support | Only ASCII characters | Supports all data types including binary |
Effect on Server State | Should not modify server state (safe method) | Can modify/create resources on server |
Idempotency | Idempotent (multiple identical requests same effect) | Not necessarily idempotent |
Usage | Data retrieval (fetching resources) | Data submission (form submission, uploads) |
Visibility | Data visible in URL | Data hidden from URL |
Use Cases and Examples
While both GET and POST are essential HTTP methods, they significantly differ in how they transmit data, impact server state, handle security, and suit various use cases, making it crucial to understand these differences for effective API design and testing.
GET Method Use Cases
The GET method is predominantly used when the goal is to retrieve data from a server without making any changes. It is widely applied in scenarios such as:
- Loading webpages: Every time a URL is entered or a link is clicked, a GET request fetches the webpage contents.
- Fetching API data: Applications use GET to obtain data, like fetching user profiles, product listings, or weather information.
- Search queries: Search engines use GET to send users’ search terms in the URL and return a list of relevant results.
- Downloading files: Whether it’s images, videos, or documents, GET is used to request and download these resources.
Example of a GET request to fetch user data via an API:
GET /users/42 HTTP/1.1
Host: api.example.com
Authorization: Bearer abc123token
The response typically contains the requested data in JSON or another format:
{
"id": 42,
"name": "Jane Doe",
"email": "jane@example.com"
}
POST Method Use Cases
POST is suited for operations where data needs to be sent to the server to create or update resources. Common use cases include:
- Submitting form data: When users fill and submit registration or login forms.
- Creating new resources: Adding a new user, POSTing a comment, or creating an order.
- Uploading files: Sending images, documents, or other large payloads to the server.
- User authentication: Securely sending login credentials to verify identity.
Example of a POST request to create a new user:
POST /users HTTP/1.1
Host: api.example.com
Authorization: Bearer abc123token
Content-Type: application/json
{
"name": "John Smith",
"email": "john@example.com"
}
The response confirms the creation of the resource:
{
"id": 43,
"name": "John Smith",
"email": "john@example.com"
}
These examples underscore the distinct purposes of GET and POST: GET for safe, read-only data retrieval, and POST for data submission that potentially modifies server state.
Get vs POST: Security Considerations in API Testing
When testing APIs, understanding the security implications of GET and POST methods is critical to protecting sensitive data and ensuring robust application behavior.
Data Exposure Risks with GET
GET requests transmit data as URL parameters, making the information visible in browser history, server logs, and network traffic, which poses a significant security risk for sensitive data such as passwords or personal information. Therefore, GET should never be used to send confidential data.
During API testing, special attention is needed to validate that sensitive parameters are not exposed in GET requests and that HTTPS is enforced to encrypt data in transit.
POST Offers Higher Privacy
POST requests encapsulate data within the request body, preventing it from appearing directly in URLs. This property makes POST a more secure choice for transmitting sensitive or extensive data like form submissions and file uploads.
However, testers must still verify that SSL/TLS encryption is active and that input validation and sanitization are rigorously applied to prevent vulnerabilities like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF).
Authentication and Access Control
Both GET and POST endpoints require secure authentication mechanisms such as token-based authentication (e.g., OAuth, JWT) to ensure that only authorized clients can access or modify resources.
API testing should include verifying proper enforcement of these mechanisms and robust handling of authentication failures.
Additional API Security Measures in Testing
Testers should check for proper use of HTTPS, rate limiting to prevent denial-of-service attacks, and ensure that error handling does not leak sensitive information.
Furthermore, POST requests should appropriately validate the content type and payload size to avoid denial-of-service or injection attacks.
In summary, while POST requests generally provide better security for sensitive operations, comprehensive API testing must include validating encryption, authentication, input sanitation, and adherence to security best practices for both GET and POST methods to mitigate security risks effectively.
Get vs POST: Performance and Practical Considerations
When choosing between GET and POST methods, understanding their performance implications and practical use cases is important for efficient API design and testing.
Performance
From a network perspective, GET requests tend to be lighter and faster because they send data as URL parameters, which are usually smaller in size. This makes GET ideal for the quick retrieval of limited data.
POST requests, by contrast, carry data in the request body, which can be larger and more complex, potentially impacting network latency.
However, the actual difference in speed between GET and POST is generally minimal under typical conditions, and server processing time largely depends on the operations triggered by the requests rather than the HTTP method itself.
Caching and Efficiency
GET requests can be cached by browsers and intermediary proxies, which significantly improves performance for repeated requests by reducing server load and network traffic.
POST requests are not cached because they often change server state, so browsers treat them as fresh requests each time.
Data Size Limitations
GET requests have URL length restrictions (typically up to 2048 characters), which limit the volume of data that can be sent.
POST requests do not have practical size limits on data sent in the body, making them ideal for uploading files, submitting forms, or complex data transmissions.
Idempotency and Safety
GET is a safe and idempotent method, meaning it should not cause any side effects on the server, and repeating the request yields the same result. This makes GET suitable for reading data repeatedly without concern for unintended consequences.
POST, on the other hand, is not idempotent by default; submitting the same POST request multiple times could create duplicate resources or trigger multiple actions.
Practical Use
In practice, GET is preferred for fetching and reading data where caching and bookmarking are beneficial. POST is best suited for operations that submit or modify data on the server.
API testing should verify that these usage patterns are correctly implemented to optimize performance and ensure expected behavior.
In summary, while GET often provides faster and more efficient data retrieval due to caching and lighter request size, POST enables handling larger and sensitive data with secure submission mechanisms, making it essential to choose wisely based on the API’s functional and performance requirements.
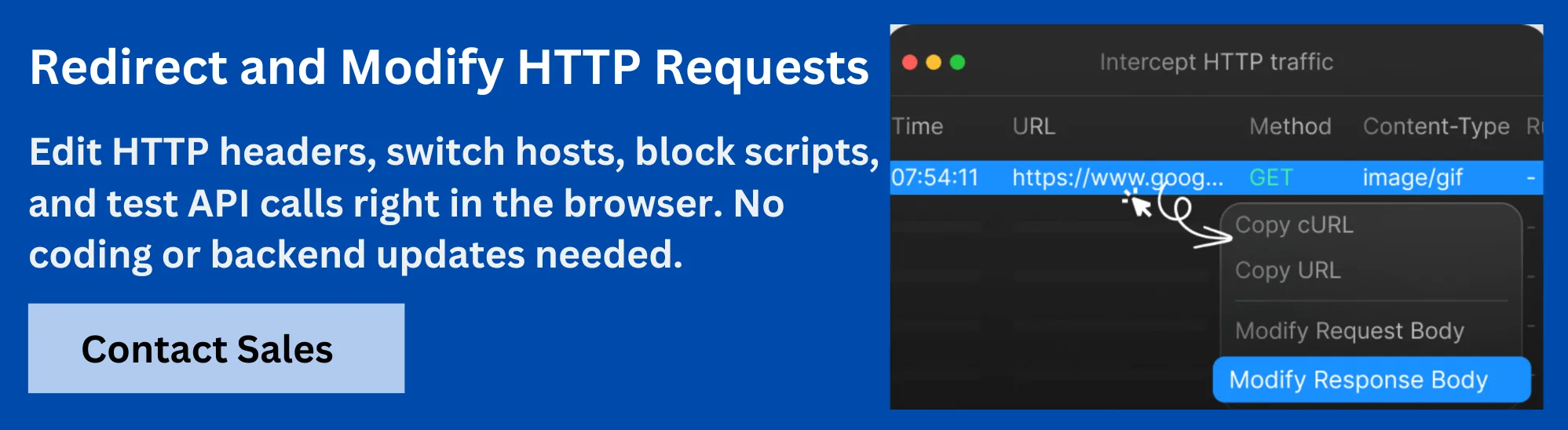
Boost API Testing with Requestly HTTP Interceptor
When working with GET and POST methods in API testing, precise control over HTTP requests and responses is crucial. Requestly HTTP Interceptor empowers developers and testers to seamlessly intercept, modify, and debug GET and POST requests in real-time, significantly enhancing testing accuracy and efficiency.
- Modify GET and POST Requests on the Fly: Requestly allows modification of URL parameters in GET requests and the request body in POST calls without changing backend code. This makes it easy to test different query parameter combinations, payloads, and headers, helping uncover edge cases or verify API behavior under various conditions.
- Simulate Real-World Scenarios: With Requestly, testers can mock responses to GET requests or manipulate POST request payloads to simulate success, failure, or timeout scenarios. This flexibility is invaluable for validating how applications handle diverse server responses for both GET and POST methods.
- Test Security and Data Handling: Requestly enables quick alteration of request headers and body content, allowing testers to verify authentication tokens, sensitive data handling, and ensure that sensitive information is not exposed inadvertently in GET requests versus POST submissions.
- Streamline Debugging of API Calls: Inspecting and modifying GET and POST requests in real-time helps isolate issues related to URL encoding, data size limitations, or header misconfigurations. Requestly’s intuitive interface makes it easier to track and debug these differences during API testing.
- Efficient Environment Switching: Easily redirect GET and POST requests between development, staging, and production environments. This eliminates the need to redeploy or hardcode environment-specific data, speeding up testing cycles.
By integrating Requestly HTTP Interceptor with GET vs POST testing workflows, teams can improve API reliability, identify vulnerabilities earlier, and ensure that both retrieval and submission methods function optimally under diverse scenarios.
Conclusion
Understanding the differences between GET and POST methods is fundamental for designing, developing, and testing efficient and secure APIs. While GET is ideal for retrieving data with its cacheability, bookmarking, and lightweight nature, POST caters better to securely submitting data and performing operations that modify server resources. Choosing the right method impacts not only performance and security but also the overall user experience and reliability of applications.
In API testing, recognizing these distinctions ensures that endpoints behave as expected under various scenarios, and tools like Requestly HTTP Interceptor can significantly enhance this process by enabling real-time request and response manipulation for both GET and POST methods. Mastery of GET vs POST helps teams build robust APIs that are both performant and secure.

Contents
- What Are GET and POST Methods?
- GET Method
- POST Method
- GET vs POST: Key Differences
- Use Cases and Examples
- GET Method Use Cases
- POST Method Use Cases
- Get vs POST: Security Considerations in API Testing
- Data Exposure Risks with GET
- POST Offers Higher Privacy
- Authentication and Access Control
- Additional API Security Measures in Testing
- Get vs POST: Performance and Practical Considerations
- Performance
- Caching and Efficiency
- Data Size Limitations
- Idempotency and Safety
- Practical Use
- Boost API Testing with Requestly HTTP Interceptor
- Conclusion
Subscribe for latest updates
Share this article
Related posts
Get started today
Requestly is a web proxy that requires a desktop and desktop browser.
Enter your email below to receive the download link. Give it a try next time you’re on your PC!