GraphQL Authentication: Essential Methods, Common Challenges, and Solutions


Authentication is a crucial aspect of securing any API, and GraphQL is no exception. It involves verifying the identity of users or clients requesting access to protected resources, ensuring that only authorized parties interact with sensitive data.
Unlike traditional REST APIs, GraphQL often uses a single endpoint for all operations, which presents unique challenges and opportunities for implementing effective authentication.
This article explores the fundamentals of GraphQL authentication, common methods for securing APIs, and practical examples to help you build robust and secure GraphQL services.
Understanding GraphQL Authentication
Authentication in GraphQL is the process of verifying the identity of users or clients to ensure secure access to protected API resources. Given GraphQL’s single-endpoint model, authentication typically involves validating tokens or credentials sent in request headers before granting access to data or operations.
It’s important to differentiate authentication, which confirms “who” the user is, from authorization, which determines “what” the user can do or access.
Common authentication approaches in GraphQL include token-based methods like JSON Web Tokens (JWT), session-based authentication with cookies, and integration with third-party providers such as OAuth or OpenID Connect.
These methods use middleware or context functions to validate credentials and pass authenticated user information to resolver functions for secure data retrieval and mutation.
Implementing robust authentication mechanisms in GraphQL not only safeguards sensitive information but also supports building personalized and permission-based user experiences across applications.
Common GraphQL Authentication Methods
Several authentication methods are commonly used to secure GraphQL APIs, each offering unique advantages depending on the application requirements:
- Token-Based Authentication: Often implemented with JSON Web Tokens (JWT), this method issues a token upon successful login. Clients include the token in the Authorization header for subsequent requests. It supports stateless interactions and is widely used for its scalability and ease of integration.
- Session-Based Authentication: Uses server-side sessions to track authenticated users, typically managed with cookies. This approach maintains user state on the server and is suited for applications where session persistence is important.
- Third-Party Authentication Providers: Integrates external identity providers via OAuth, OpenID Connect, or social logins like Google and Facebook. This method offloads user authentication, enhancing user experience and security.
- Custom Authentication Middleware: Developers can build bespoke authentication logic to fit unique business rules or multi-factor authentication requirements, offering high flexibility.
Each method can be integrated into GraphQL by validating credentials in middleware or context functions before processing queries or mutations. Choosing the right authentication approach depends on factors like application architecture, user experience goals, and security compliance needs.
Implementing Authentication in GraphQL
Implementing authentication in GraphQL typically involves integrating verification logic within the request handling pipeline to confirm user identity before executing queries or mutations. Common implementation steps include:
- Using Authorization Headers: Clients send tokens (e.g., JWT) in the Authorization header of GraphQL requests. The server extracts and validates these tokens to authenticate the user.
- Middleware-Based Authentication: Middleware functions intercept incoming requests to verify authentication credentials before they reach resolvers. This centralizes authentication logic and prevents unauthorized access early in the request lifecycle.
- Context Integration: Authenticated user information is added to the GraphQL context object, making it accessible to resolver functions for enforcing access control and personalization.
- Schema-Level Directives: Custom directives can be defined to annotate schema fields or operations with authentication requirements, enabling declarative access controls directly in the schema.
- Combining Authentication and Authorization: While authentication verifies identity, authorization defines what an authenticated user can access or modify. Implementations often intertwine both by checking permissions within resolvers based on authenticated user roles.
Role-Based Access Control and Authorization
Role-Based Access Control (RBAC) is a widely used strategy for managing user permissions in GraphQL APIs. It involves assigning users specific roles, such as admin, editor, or viewer, and granting permissions based on these roles to control access to queries, mutations, and fields.
RBAC implementation typically includes:
- Defining user roles and corresponding permissions in the schema or configuration
- Applying role checks in resolver functions or middleware to enforce access rules
- Using tools like graphql-shield or graphql-rbac to create declarative permission layers based on roles
- Differentiating between authentication (identity verification) and authorization (permission to perform actions)
Field-level authorization enables fine-grained control by restricting access to specific fields within types, protecting sensitive information even from authorized users without the necessary permissions.
Alternatively, Attribute-Based Access Control (ABAC) is gaining traction, where attributes such as user department, location, or time of access determine permissions, allowing more complex and dynamic access policies.
Proper RBAC implementation ensures secure, maintainable, and scalable authorization that aligns with real-world organizational roles and policies, protecting sensitive data while supporting diverse user needs.
Common Challenges and Solutions in GraphQL Authentication
GraphQL authentication presents unique challenges that require thoughtful solutions to ensure secure, reliable, and scalable API access. The following points highlight common issues and ways to effectively address them.
1. Single Endpoint Complexity
- Challenge: Since GraphQL uses a single endpoint for all operations, distinguishing between authenticated and unauthenticated requests or different resource access levels can be tricky.
- Solution: Implement middleware that parses operation names or query contents and enforce authentication rules appropriately per operation.
2. Managing Subscriptions Authentication
- Challenge: Real-time subscriptions require persistent connections, making token expiration and refresh more complex.
- Solution: Use secure, time-limited tokens with mechanisms to refresh or renegotiate authentication during active subscriptions.
3. Balancing Stateless and Stateful Sessions
- Challenge: Stateless JWT tokens are scalable but harder to revoke, while session-based auth simplifies revocation but adds server overhead.
- Solution: Combine short-lived JWT tokens with refresh tokens or implement token blacklisting mechanisms to maintain security without sacrificing scalability.
4. Granular Authorization
- Challenge: Enforcing fine-grained control at field or operation levels often requires complex logic.
- Solution: Utilize libraries like graphql-shield for declarative permission rules and organize authorization logic clearly between middleware and resolvers.
5. Secure Token Handling
- Challenge: Storing and transmitting tokens insecurely can expose vulnerabilities.
Solution: Always use HTTPS, store tokens securely (e.g., HttpOnly cookies), and follow best practices to prevent XSS and CSRF attacks.
6. Error Handling and Debugging Authentication Failures
- Challenge: Problems diagnosing why authentication fails can slow development.
- Solution: Implement detailed logging, consistent error messages, and debugging tools to trace the authentication flow effectively.
Addressing these typical challenges with proven strategies ensures robust, secure, and user-friendly authentication for GraphQL APIs.
Practical Examples and Code Snippets
Below are some practical implementations to help understand how GraphQL authentication can be coded:
Example: JWT Authentication
const jwt = require('jsonwebtoken');
const SECRET_KEY = 'your-secret-key';
// Middleware to authenticate token
const authenticate = (req, res, next) => {
const token = req.headers.authorization?.split(' ')[1];
if (!token) {
throw new Error('Authentication token missing');
}
try {
const user = jwt.verify(token, SECRET_KEY);
req.user = user;
next();
} catch (err) {
throw new Error('Invalid/Expired token');
}
};
Integrating OAuth with GraphQL
Using OAuth providers (e.g., Google) to authenticate:
- Redirect users to the OAuth consent screen.
- Receive authorization code and exchange for access token.
- Validate token and extract user info.
- Use user info in GraphQL context to authorize API requests.
Role-Based Access Control with graphql-shield
const { shield, rule, allow } = require('graphql-shield');
const isAuthenticated = rule()((parent, args, ctx) => {
return ctx.user !== null;
});
const isAdmin = rule()((parent, args, ctx) => {
return ctx.user.role === 'admin';
});
const permissions = shield({
Query: {
users: isAuthenticated,
adminData: isAdmin,
},
});
These snippets illustrate essential patterns for secure authentication and authorization in GraphQL, allowing developers to tailor them according to specific security requirements and user management strategies.
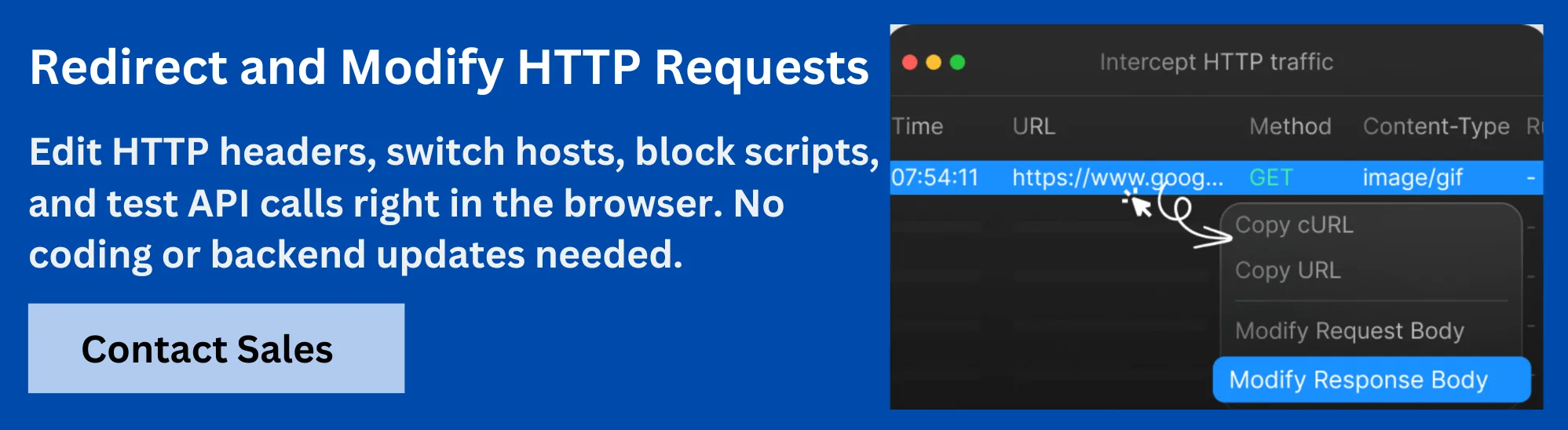
Enhance GraphQL Authentication Testing with Requestly HTTP Interceptor
Requestly HTTP Interceptor is a versatile tool that simplifies testing and debugging of GraphQL authentication flows. It enables developers to intercept, modify, and mock authentication requests and responses on the fly without needing backend changes.
Key benefits include:
- Mock Authentication Scenarios: Simulate successful and failed login attempts by modifying token payloads and response statuses in real-time.
- Test Error Handling: Inject custom error messages or delays to validate how your client handles authentication errors, such as expired tokens or permission denials.
- Environment Switching: Redirect authentication requests between development, staging, and production servers seamlessly to test across environments.
- Custom JavaScript Rules: Write scripts to dynamically alter headers, tokens, or response bodies based on test cases or user roles.
- Collaboration-Friendly: Share HTTP rules instantly across teams to ensure consistent testing setups and faster issue resolution.
By integrating Requestly HTTP Interceptor into your GraphQL authentication testing workflow, teams can accelerate development, catch security gaps early, and deliver more reliable and secure APIs.
Conclusion
Securing GraphQL APIs with strong authentication and authorization mechanisms is essential to protect sensitive data and maintain user trust. By understanding common authentication methods like JWT, OAuth, and session-based approaches, and implementing role-based access control, developers can create flexible and secure API environments.
Addressing typical challenges with best practices and leveraging powerful tools like Requestly HTTP Interceptor for testing and debugging further enhances API reliability and developer efficiency. As GraphQL continues to evolve, adopting these security fundamentals ensures robust, scalable, and user-friendly API experiences.

Contents
- Understanding GraphQL Authentication
- Common GraphQL Authentication Methods
- Implementing Authentication in GraphQL
- Role-Based Access Control and Authorization
- Common Challenges and Solutions in GraphQL Authentication
- Practical Examples and Code Snippets
- Enhance GraphQL Authentication Testing with Requestly HTTP Interceptor
- Conclusion
Subscribe for latest updates
Share this article
Related posts