How to use Block list in Charles Proxy

Your lightweight Client for API debugging
No Login Required
Requestly is a web proxy that requires a desktop and desktop browser.
Enter your email below to receive the download link. Give it a try next time you’re on your PC!










Introduction
During local development you might want to block access to external APIs to simulate an offline environment. It further complicates the process when you want to avoid unintended calls to production services to prevent additional billing.
“Block List” comes handy in such cases where you can block network responses from your backend without making any changes to your codebase.
Setting up Block List in Charles Proxy is a little complex. You can follow the steps below to configure Block List with ease.
A Browser Extension, that just needs you to fill 1 field and doesn’t have VPN issues, is also explained later in this post. You can also use that in place of Charles Proxy.
Charles Proxy's Block List Tool: How It Works
The Block List feature in Charles Proxy allows you to block specific network requests, preventing them from reaching the server. This can be useful for testing how your application behaves when certain resources (like APIs or scripts) are unavailable.
How to Configure Charles Proxy’s Block List Tool
- Open Charles Proxy and ensure that your proxy is enabled and traffic is being captured.
- Navigate to the Tools Menu:
- In the top menu, click on Tools.
- From the dropdown, select Block List.
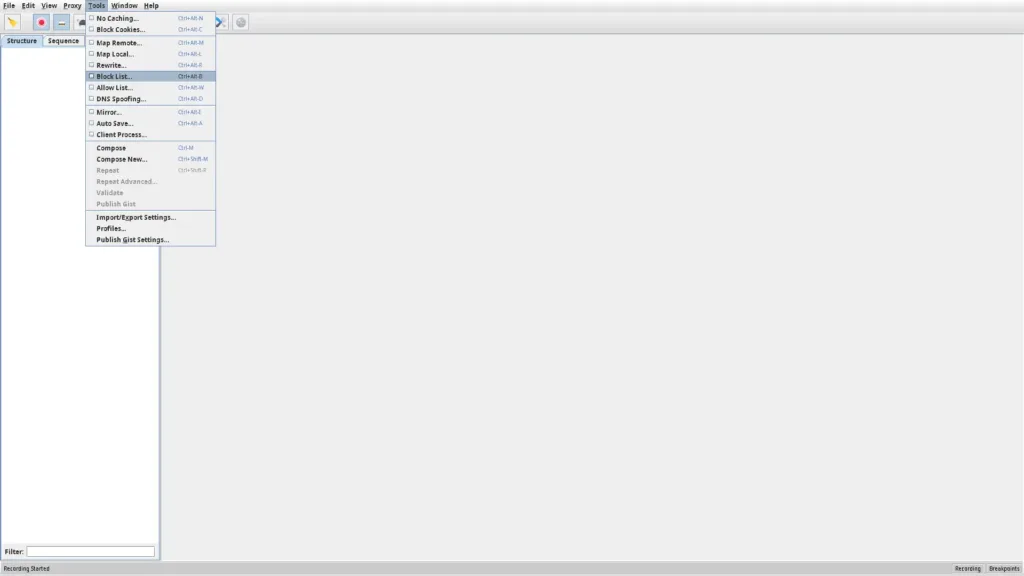
- This will open the Block List settings window Here check Enable Block List box and select Blocking action.
- Drop Connection – this option will simulate a network error for the request
- Return 403 – This option will return a 403 (forbidden) status code as response
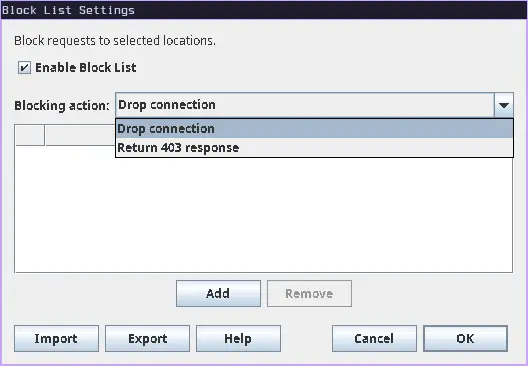
Now click on add to add a new url:
- Protocol: Here you can select your site’s protocol http or https
- Host: Here you can enter the host/domain that you want to apply the rule to.
- Port: You can specify the port on which your site is running.
- Path: Define the path if you want the rule to apply only to specific paths on the host.
- Query: here you can define the query parameters which should be targeted.
Now Save the rule by clicking OK.
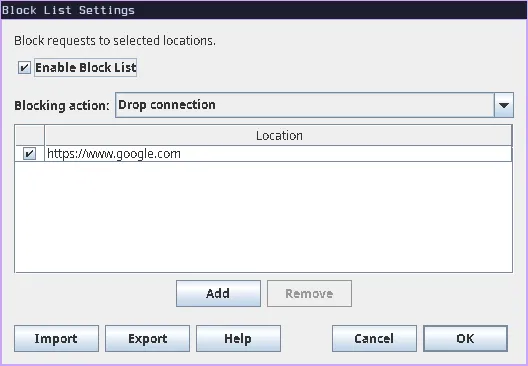
After saving this you should be able to see the rule and its modifications
Now visit the site you selected and you can see the URL change.
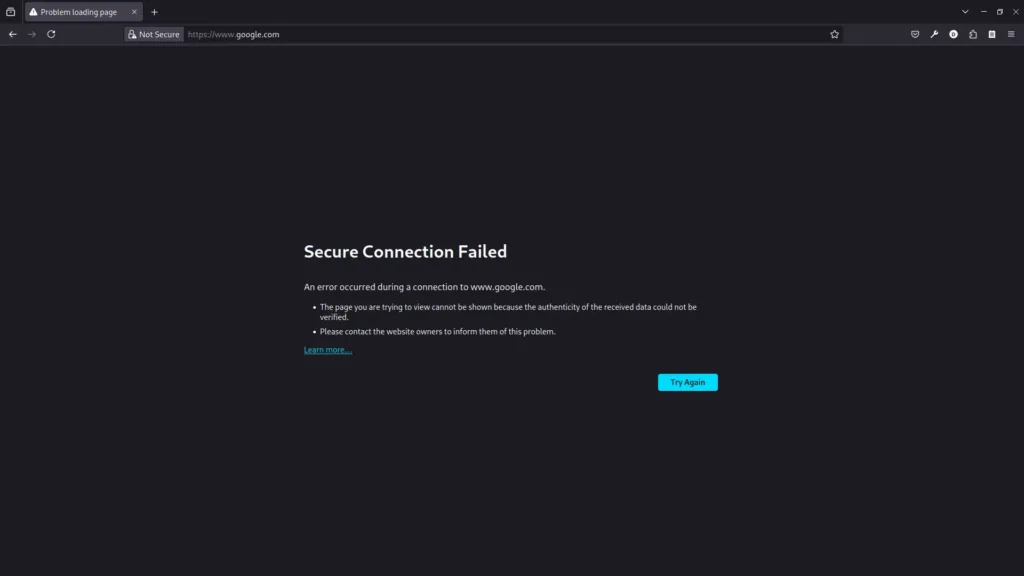
I hope you are able to configure Block list tool, if you are facing issues in setup of SSL read about SSL setup on Charles Proxy official documentation.
Due to this complicated setup process of Charles Proxy and issues with VPN we, at Requestly, came up with a smart solution. We developed a Browser Extension that can sit inside the browser and use browser’s APIs to intercept and modify your network requests and responses.
Cancel request rule in Requestly
Requestly is designed differently so it doesn’t need any SSL configuration and hence works seamlessly with your VPNs. Block List is simplified as “Cancel Request Rule” in Requestly. With just 1 input, i.e. source URL matching condition, you can block any network response to your desired value.
There are more advanced rules in Requestly & other features to help you test the working of the rule along with details of how to use this rule are explained below.
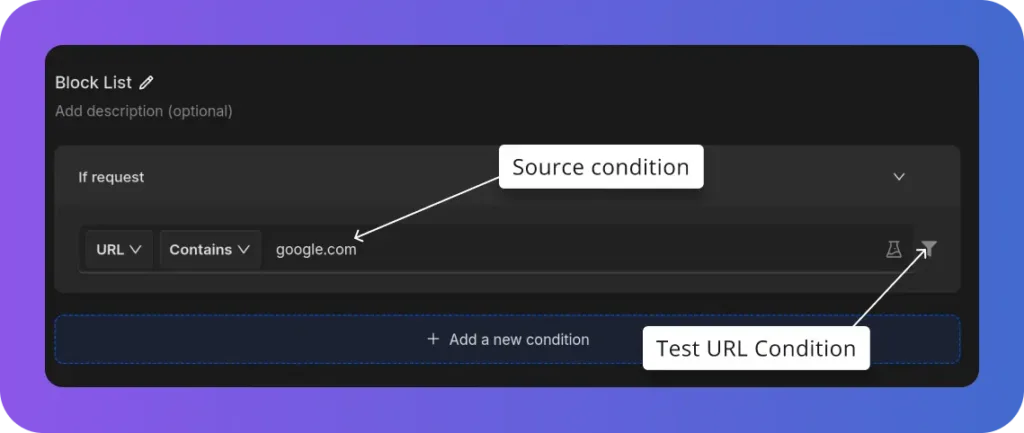
- Source Condition: Here you specify the url pattern for which the request should be blocked.
- Test URL Condition: You can check if the rules you’ve set up work correctly by testing them on specific URLs.
Steps to Configure Requestly’s Cancel Request Rule
- Install Requestly Extension: Download and install Requestly’s browser extension.
- Open Requestly Dashboard: Visit app.requestly.io and log in.
- Click on the Rules tab and then select New Rule.
- Choose Cancel Rule as the rule type.
- Enter the URL pattern in the Source Condition field.
- Name your rule and click Save.
Now you can test the rule on your desired website, or if you do not want to go through the hassle of setting it up yourself, we have created a shared list of this rule for disabling cache for you. Go ahead and import it by clicking this button below.
Or create your own Rule by following the setups below
Other Use Cases for Requestly’s Cancel request Rule
Here are some key use cases for the Block Request rule in Requestly:
- Security Testing: Block outgoing requests to simulate how your application behaves when certain endpoints are unreachable, helping to test error handling and fallback mechanisms.
- Dependency Isolation: Block requests to third-party services to test how your application functions when external dependencies are unavailable.
Migrate from Charles proxy
If you’re already using Charles Proxy, Requestly provides an easy way to import your settings. Follow the guide to migrate: Migrate from Charles Proxy.
Conclusion
I hope you have got a clear understanding of both the Block List tool in Charles Proxy and how Requestly can achieve the same results with greater ease. While Charles Proxy effectively handles the task, Requestly offers a modern, simple and efficient experience.
Since Requestly operates directly from your browser and leverages built-in browser APIs, there’s no need for complex SSL configurations, eliminating the VPN issues often encountered with Charles Proxy. Plus, you don’t need to switch between different tools — everything you need is right in your browser.
Love for Requestly is reflected in its 4.4 ⭐ rating from over 1,200 users on the Chrome Web Store. Requestly is being used by 200K+ developers across the world.
Happy Debugging!!!
Explore More
Contents
Subscribe for latest updates
Share this article
Related posts
Get started today
Requestly is a web proxy that requires a desktop and desktop browser.
Enter your email below to receive the download link. Give it a try next time you’re on your PC!




















