What Are API Keys? A Guide to Authentication and Security

APIs allow applications to communicate with each other. To control and secure access, APIs often require a method to identify the client making the request….
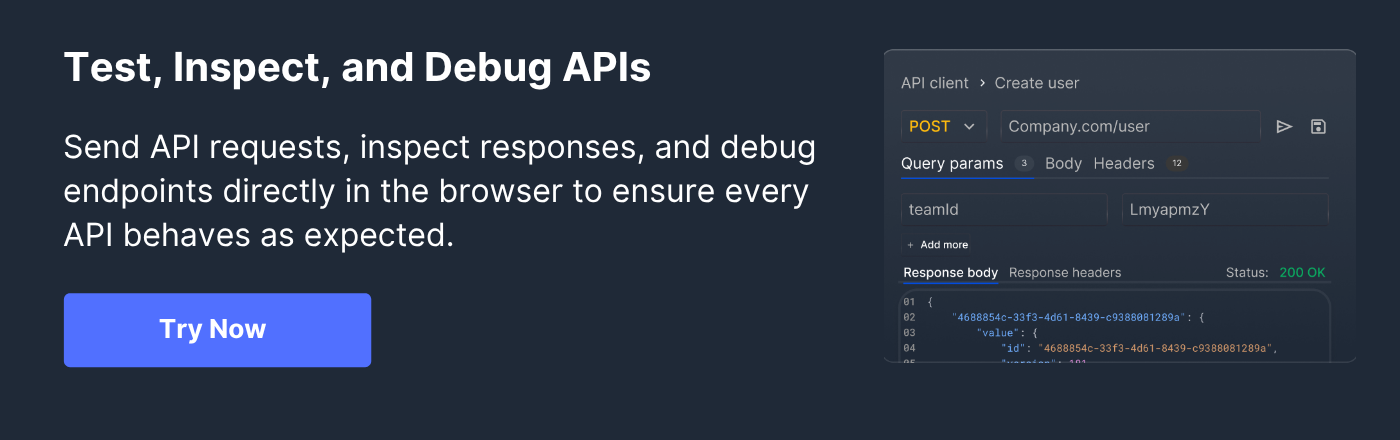
Your lightweight Client for API debugging
No Login Required
Requestly is a web proxy that requires a desktop and desktop browser.
Enter your email below to receive the download link. Give it a try next time you’re on your PC!










APIs allow applications to communicate with each other. To control and secure access, APIs often require a method to identify the client making the request. API keys are one of the most common methods for authentication. They are unique strings that link a client to the API, ensuring only authorized users can access certain resources.
When an application sends a request to an API, the key is checked against a database. If the key is valid, the API processes the request. If not, the request is rejected. API keys can also help track usage, enforce limits, and log requests for monitoring purposes.
This article explains what API keys are, how they work, when to use them, their risks, and best practices for managing them.
What Is an API Key and How Does It Work?
An API key is a unique identifier assigned to a client or application to authenticate with an API. It is typically a long string of letters and numbers that the server uses to verify that the request comes from an authorized source.
API keys are sent along with the request, usually in the header or as a query parameter. The server validates the key and determines whether the request should proceed. This process is straightforward but essential to prevent unauthorized access.
Here are the main points to understand about API key functionality:
- Authentication: Confirms the client is allowed to use the API.
- Usage tracking: Logs requests to monitor consumption and identify abnormal patterns.
- Access control: Enables different permission levels depending on the key.
- Rate limiting: Helps prevent misuse by limiting how many requests a key can make.
Why API Keys Are Important
API keys provide a simple yet effective way to control who can use your API, track usage, and enforce limits without implementing full user authentication.
Below are the key reasons API keys are essential:
- Access control: API keys ensure that only registered clients or applications can interact with your API. They help prevent unauthorized access to endpoints and sensitive resources.
- Usage tracking: API keys allow monitoring of API requests by client, application, or project. This helps identify high-usage clients, unusual activity, or potential abuse.
- Rate limiting and quotas: Keys make it possible to limit how many requests a client can make within a given time. This protects the API from overload and ensures fair usage across clients.
- Billing and monetization: For paid APIs, keys link requests to a specific client account, enabling accurate billing based on usage.
- Simplified integration: API keys provide a lightweight authentication method that developers can implement quickly without complex authentication flows.
- Audit and debugging: By tying requests to a key, developers can trace issues back to the client or application, improving support and debugging processes.
When to Use API Keys in Your Application
API keys are most effective in scenarios where client identification, usage tracking, and basic access control are needed. They are best suited for server-to-server communication, internal applications, and public APIs with non-sensitive data.
Below are the key situations where using API keys makes sense:
- Server-to-server communication: When two backend services need to exchange data securely, API keys provide a straightforward way to authenticate requests without involving user credentials.
- Public APIs with limited access: For APIs that expose read-only or non-critical data, keys allow developers to use the API while preventing anonymous or unmonitored usage.
- Monitoring and analytics: API keys help track which applications are calling your API, how often, and which endpoints they use, allowing better usage insights and resource planning.
- Rate-limited endpoints: Keys enable enforcing request limits per client, preventing abuse and ensuring that the API remains available and performant for all users.
- Feature-based access control: Different keys can grant access to specific endpoints or features, helping manage tiered services or subscriptions without complex authentication mechanisms.
- Internal application access: Within an organization, keys can control access between microservices, internal tools, or scripts while maintaining security and accountability.
Understanding API Key Generation and Validation
API key generation and validation involve multiple steps that define how an API controls access, enforces security, and tracks usage.
Here is how you can generate, validate, and manage API keys effectively.
Step 1: Generating a Unique API Key
The API provider generates a unique string for each client or application. This string is typically long and random, created using cryptographically strong algorithms. The unpredictability of the key prevents attackers from guessing valid keys. The key’s structure and length directly affect its security, particularly for public or high-value APIs.
Step 2: Associating the Key with a Client
Once generated, the key is linked to a specific client, application, or project in the provider’s database. This association allows the API to identify the source of each request, track usage, and apply permissions or limits specific to that client. The key essentially serves as the application’s identity in the system.
Step 3: Validating the Key on Each Request
Every API request is checked against the stored keys. Validation includes confirming the key exists, is active, has not expired, and has the required permissions. Without validation, unauthorized requests could bypass access controls. Some APIs also include rate-limit checks during validation to prevent misuse.
Step 4: Managing Key Expiration and Rotation
Temporary or rotating keys reduce the risk associated with key exposure. Expiration limits the window during which a compromised key can be exploited, while rotation ensures keys are refreshed periodically. Automated rotation reduces administrative overhead and improves security hygiene.
Step 5: Revocation and Lifecycle Management
Keys can be deactivated at any time if misuse or exposure is detected. Proper lifecycle management tracks creation date, last usage, and modifications. Stale or unused keys are removed to prevent potential security risks.
Step 6: Enforcing Scope and Permissions
Advanced APIs allow keys to have specific scopes or permissions. These controls restrict which endpoints the key can access, what operations it can perform, or which data it can retrieve. Proper scoping reduces the potential impact of a compromised key.
Step 7: Logging and Monitoring Usage
All key activity is logged to support auditing, troubleshooting, and anomaly detection. Unusual patterns, such as requests at unexpected times or unusually high volumes, can indicate misuse or security threats. Monitoring ensures proactive responses to potential issues.
Step 8: Secure Implementation Practices
Even with strong generation and validation, improper handling can compromise security. Keys should never be hardcoded in client-side code, should be stored securely, and must always be transmitted over encrypted channels. These practices safeguard the API from inadvertent exposure.
How to Manage and Store API Keys
Proper management and storage of API keys is essential to maintain security, prevent unauthorized access, and reduce operational risk. Mismanagement can lead to data breaches, service misuse, or system downtime.
Here is how you can handle API keys effectively:
Step 1: Store Keys Outside the Codebase
Never hardcode API keys in your application code. Instead, store them in environment variables, configuration files secured on the server, or dedicated secret management systems. Keeping keys out of the codebase prevents accidental exposure through version control or public repositories.
Step 2: Use Secret Management Tools
Secret management solutions, such as vaults or cloud-based key managers, provide centralized storage with encryption and access control. These tools often include audit logs, automated rotation, and fine-grained permissions, reducing manual handling risks.
Step 3: Limit Access to Keys
Restrict key access to only the components or team members that need it. Avoid sharing keys via email or chat, and use role-based access controls to minimize the chance of unauthorized use. Limiting exposure reduces the risk of accidental leaks or misuse.
Step 4: Rotate Keys Regularly
Keys should be rotated periodically, especially if they are exposed in logs or development environments. Rotation ensures that even if a key is compromised, it has a limited window of exploitation. Automating rotation reduces administrative overhead and ensures consistency.
Step 5: Apply Scope and Permission Controls
Where possible, assign specific scopes or permissions to each key. For example, a key used for reading data should not have write or delete permissions. Granular permissions minimize potential damage if a key is compromised.
Step 6: Monitor and Audit Key Usage
Track all API key activity in logs. Monitoring helps detect unusual patterns, such as spikes in usage, requests from unexpected IP addresses, or attempts to access restricted endpoints. Regular audits improve security posture and support troubleshooting.
Step 7: Secure Transmission
Always transmit API keys over encrypted channels, such as HTTPS. Plaintext transmission exposes keys to interception and increases the likelihood of unauthorized access. Enforcing encryption ensures safe communication between clients and the API.
Step 8: Revoke Compromised Keys Immediately
If a key is suspected to be exposed or misused, revoke it immediately. Follow up with generating a new key and updating the affected client or service. Prompt revocation prevents further unauthorized requests and limits potential damage.
Key Security Risks of API Keys
API keys are a basic authentication tool, but they carry security risks that can affect both functionality and data protection. Below are the main risks:
- Exposure through code or repositories: Hardcoding API keys in client-side code or storing them in public repositories makes them accessible to anyone who can view the code. Attackers can extract the key and make unauthorized requests.
- Insecure sharing: Sending keys via email, chat, or other unencrypted channels increases the chance of interception or accidental leaks.
- Limited access control: API keys identify the application, not individual users. This makes it difficult to enforce user-specific permissions or track misuse at a user level.
- Replay attacks: If a key is intercepted, attackers can reuse it to repeatedly access the API. This can result in excessive resource consumption, service disruption, or unauthorized operations.
- Transmission without encryption: Sending API keys over unencrypted channels exposes them to network sniffing or man-in-the-middle attacks. Secure protocols like HTTPS are essential to protect keys in transit.
- Static keys and lack of rotation: Keys that are never rotated remain vulnerable indefinitely. Without regular rotation, a compromised key can be exploited for extended periods.
- Insufficient monitoring: Without logging and auditing key usage, unusual activity can go unnoticed, increasing the risk of misuse and delaying response to security incidents.
Why Use Requestly for API Key Testing
Testing API keys effectively is crucial to ensure secure and reliable application behavior. Requestly offers a suite of tools designed to facilitate comprehensive API key testing without impacting production environments.
Here are the key capabilities Requestly provides for API key testing:
- Simulate API Requests with Custom Headers: Send HTTP requests with specific API keys to test authentication and authorization mechanisms. This allows for validation of access controls and permission settings.
- Modify Request Headers Dynamically: Easily add, remove, or modify API key headers in real-time to test different access scenarios and ensure the application responds appropriately.
- Mock API Responses: Simulate various API responses, including success, failure, and error states, to test how your application handles different outcomes without making actual API calls.
- Automate API Testing with Scripts: Utilize pre-request and post-response scripts to automate testing workflows, validate response data, and handle dynamic scenarios programmatically.
- Monitor API Key Usage: Track and log API key usage to identify potential misuse or unauthorized access attempts, aiding in security audits and compliance.
Conclusion
API keys provide a simple yet effective method to control access, monitor usage, and secure API integrations. While they are easier to implement than full authentication systems, their effectiveness depends on proper generation, validation, management, and monitoring. Requestly helps developers safely test API key authentication, validate permissions, and simulate scenarios without affecting production systems.

Contents
Subscribe for latest updates
Share this article
Related posts
Get started today
Requestly is a web proxy that requires a desktop and desktop browser.
Enter your email below to receive the download link. Give it a try next time you’re on your PC!