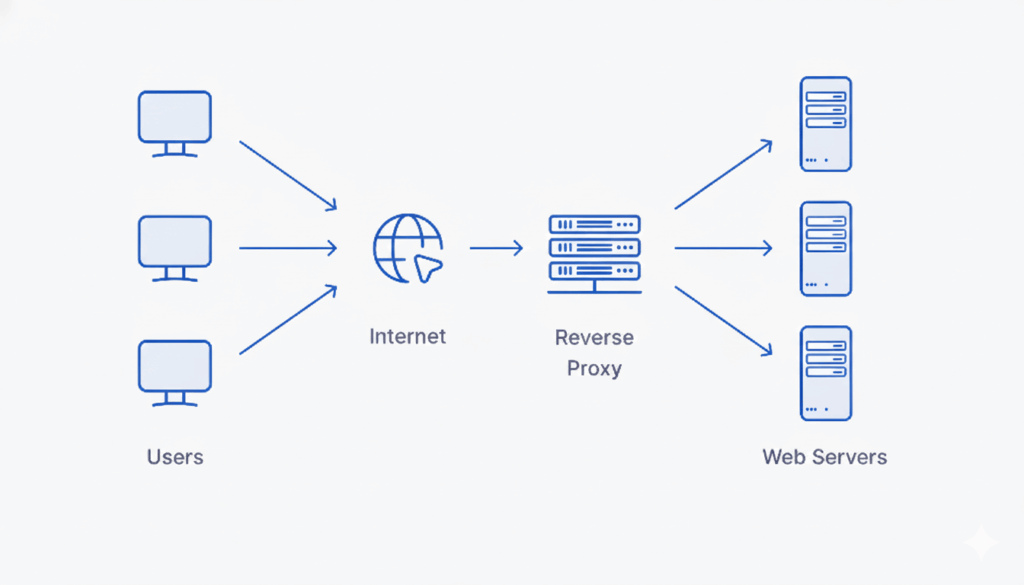
A reverse proxy sits in front of your backend servers and becomes the main point where all incoming requests arrive. Users never connect to your application servers directly because the reverse proxy handles the request first. It decides which backend should process it, whether anything needs to be filtered or modified, and whether the request should reach the application at all.
Before diving into how reverse proxies work, it helps to understand what a proxy is and how the reverse version differs from it.
Understanding a Proxy (Forward Proxy)
A forward proxy sits between the client and the internet and makes requests on behalf of the user. Instead of the client connecting directly to a website or API, the forward proxy handles the communication.
Here’s what happens when you browse through a forward proxy:
Your request goes to the proxy first
The proxy forwards the request to the destination
The website only sees the proxy’s IP, not yours
You gain anonymity or bypass access restrictions
Forward proxies are common in corporate networks to control and monitor employee browsing. Individuals also use them to hide their identity or access region-blocked content. VPNs take this idea further with encryption and routing, but the core concept is the same.
Moving to a Reverse Proxy (and How It Differs)
A reverse proxy flips the idea entirely. Instead of acting on behalf of the client, it acts on behalf of the server.
A reverse proxy sits in front of your backend servers, and every incoming request goes to it first. The backend servers are never exposed directly to users.
It handles tasks like:
Deciding which backend server should process a request
Filtering, blocking, or modifying requests
Handling caching and SSL
Protecting internal architecture details
To make it clear:
Forward proxy = hides the client
Reverse proxy = hides the server
Why Reverse Proxies Are Used
Reverse proxies exist because a single application server cannot handle everything on its own. Modern websites and APIs need:
A reverse proxy becomes the control center that helps achieve all of this.
Let’s break down the major use cases.
How Reverse Proxies Are Used
1. Load Balancing Across Multiple Servers
A reverse proxy sits between the client and your backend servers.
It receives every incoming request first, then decides which server should handle it.
This lets you spread the load instead of dumping everything on one machine.
Here’s the flow:
Client → Reverse Proxy → Backend Server A/B/C
The reverse proxy uses load balancing strategies to determine which server should handle each request.
Common strategies include:
By evaluating the current load on each server, the proxy ensures requests are distributed efficiently, keeping your system fast, stable, and reliable even during traffic spikes.
2. Security and Privacy for Backend Servers
Directly exposing your backend servers to the internet is risky.
A reverse proxy acts as a protective layer, sitting between clients and your servers, and handling all incoming traffic first.
Here’s how it helps:
Hides backend IP addresses – clients and attackers never see your real server IPs
Blocks malicious traffic – filters requests with suspicious patterns
Stops bots and scrapers – prevents automated attacks or unwanted crawlers
Mitigates DDoS attacks – absorbs traffic spikes before they reach the backend
Enforces authentication and rate limits – ensures only valid users or requests get through
Adds or modifies security headers – strengthens HTTP response security
Terminates SSL/TLS connections safely – centralizes encryption and reduces load on backend servers
When an attack occurs, it hits the reverse proxy first, keeping your application servers safe and isolated from direct exposure.
3. Caching for Speed and Reduced Load
A reverse proxy can store cached copies of pages, images, and even API responses.
When another user requests the same content, the proxy serves it immediately, without contacting the backend server.
How this helps:
Faster responses – pages and APIs load more quickly
Lower backend load – reduces database and CPU usage
Handles traffic spikes – multiple users can get content from the cache simultaneously
Reduces infrastructure costs – fewer requests reach your servers
Content Delivery Networks (CDNs) work on this principle. They are essentially large, distributed reverse proxies that deliver cached content globally, ensuring high speed and reliability for users everywhere.
4. Routing in Microservices Architectures
In a microservices architecture, different endpoints are handled by separate services.
A reverse proxy acts as a central gateway, routing requests to the correct service automatically.
Example routing:
This allows clients to interact with a single entry point, while the proxy distributes requests to the appropriate backend services.
Even if your system is split across dozens of microservices, the reverse proxy keeps the architecture unified and manageable.
Popular Reverse Proxy Tools and Servers
These tools sit between users and your backend infrastructure, handling routing, security, caching, load balancing, and traffic management. Each one has different strengths depending on whether you need high performance, easy configuration, horizontal scaling, or full-featured edge security.
1. NGINX
A high performance reverse proxy known for speed, low memory usage, and flexible configuration. Commonly used for TLS termination, load balancing, caching, and API gateway patterns.
2. HAProxy
One of the most reliable load balancers on the planet. Extremely strong at handling huge traffic volumes, health checks, connection pooling, and advanced routing logic.
3. Traefik
A modern reverse proxy built for microservices and containers. Auto-discovers services from Docker, Kubernetes, Nomad, and Consul which makes setup extremely simple for dynamic environments.
4. Apache HTTP Server
Used in older or enterprise systems where Apache is already installed. Offers reverse proxy capabilities via modules like mod_proxy, mod_ssl, and mod_cache.
5. Cloudflare (Reverse Proxy at the Edge)
Works as a global reverse proxy in front of your entire application. Provides DDoS protection, caching, WAF rules, bot mitigation, and global routing without touching your servers.
Conclusion
A reverse proxy is a critical component of modern web architecture.
Sitting in front of your backend servers, it enhances performance, security, scalability, and reliability. Almost every major website and API relies on a reverse proxy, even if users never see it.
Understanding how reverse proxies work gives insight into how large-scale platforms stay fast, secure, and highly available, even under massive traffic and complex architectures.