What is HTTP: Methods, Headers, and How It Works

Your lightweight Client for API debugging
No Login Required
Requestly is a web proxy that requires a desktop and desktop browser.
Enter your email below to receive the download link. Give it a try next time you’re on your PC!










Most developers and testers work with HTTP (Hypertext Transfer Protocol) directly or indirectly every day, whether they’re sending a form, fetching an API response, or debugging a failed call. It is the protocol behind nearly everything that moves data across the web. This includes browsers, APIs, webhooks, mobile apps, and even some databases.
This article explains how HTTP works, breaks down the core methods, covers key headers, and provides practical context that helps testers and engineers use it effectively in real scenarios.
What Is HTTP?
HTTP (Hypertext Transfer Protocol) is a stateless, application-layer protocol used for transmitting data over the web. It follows a request-response model where a client (usually a browser or an API client) sends a request to a server, and the server returns a response. It uses TCP (or sometimes UDP in HTTP/3) as the underlying transport protocol.
HTTP doesn’t store any state between requests. Each request is independent, and the server doesn’t remember previous interactions. This stateless design makes HTTP simple and scalable, but it also requires mechanisms like cookies or tokens to maintain sessions.
There are several versions of HTTP in use today:
- HTTP/1.1: Still widely used; processes one request per TCP connection
- HTTP/2: Supports multiplexing and header compression to improve performance
- HTTP/3: Built on QUIC (UDP-based), improving connection setup and latency
Each version introduces optimizations at the transport and protocol layers.
How HTTP Handles Requests and Responses
Every HTTP interaction involves a client and a server. The client sends a request, and the server sends a response. Here’s what each part typically includes:
HTTP Request Structure:
- Method: Tells the server what action to perform (e.g., GET, POST)
- URL: Specifies the resource being requested
- Headers: Pass metadata (e.g., content type, authentication)
- Body: Optional; included mainly in methods like POST or PUT to send data
HTTP Response Structure:
- Status Line: Includes the HTTP version and status code (e.g., 200 OK)
- Headers: Similar to request headers; control caching, content type, etc.
- Body: Contains the response data, such as HTML, JSON, etc.
Every request and response also includes metadata in the form of headers.
Core HTTP Methods and Status Codes
HTTP methods define what action the client wants the server to perform. Each method is intended for a specific type of operation:
Common HTTP Methods:
- GET: Fetch a resource without changing it. Should be idempotent.
- POST: Submit data to the server, usually causing a change in state or side effect.
- PUT: Replace a resource with the data provided.
- PATCH: Partially update a resource.
- DELETE: Remove a resource.
- HEAD: Same as GET but returns only headers.
- OPTIONS: Returns supported HTTP methods for a resource.
Common HTTP Status Codes:
- 200 OK: Request succeeded
- 201 Created: Resource successfully created (used with POST)
- 204 No Content: Request succeeded, no body returned
- 301 Moved Permanently: Resource has a new permanent URI
- 400 Bad Request: Client sent malformed request
- 401 Unauthorized: Authentication required
- 403 Forbidden: Authenticated but not allowed
- 404 Not Found: Resource not available
- 500 Internal Server Error: Server failed to process the request
- 502 Bad Gateway / 503 Service Unavailable: Upstream or server-side issues
A 204 or 304 response can be misinterpreted by JavaScript-based frontends if not handled correctly. For example, a 204 (No Content) should not trigger rendering logic, and a 304 (Not Modified) assumes the browser or client can serve content from cache. If the frontend expects a body but receives none, it can break UI logic or error handling flows.
Role of Headers in Data Exchange and Caching
HTTP headers carry metadata that controls how requests and responses behave. They sit outside the body but often determine how the body is interpreted, validated, cached, compressed, or even whether the body is processed at all. For developers and testers, headers are critical for controlling behavior across APIs, clients, proxies, and caches.
There are two broad categories:
- Request headers: Sent by the client to provide context about the request.
- Response headers: Sent by the server to instruct the client on how to handle the response.
Let’s look at the core functions of headers in data exchange and caching.
1. Headers That Control Content Negotiation
These headers affect how the server formats the response and how the client parses it.
- Accept: Tells the server what content types the client can handle (e.g. application/json, text/html). The server uses this to return the correct format.
- Content-Type: Specifies the media type of the request or response body. If a client sends data, this tells the server how to parse it. If the server responds, this tells the client how to handle the response.
- Accept-Encoding/Content-Encoding: Controls compression. Clients can specify support for gzip or br and servers can compress accordingly.
For example, if the Content-Type is misdeclared (for example, sending JSON with text/plain), clients may reject or mishandle the response. Testers often catch mismatches between Content-Type and body format.
2. Headers That Affect Caching
Caching is where headers become especially important and easy to misconfigure. Caching decisions are not just made by browsers, but also by reverse proxies like Nginx, CDNs like Cloudflare, and mobile apps with their own cache layers.
- Cache-Control: The most critical caching header. Controls how long content is considered fresh. Example values:
- no-cache: Revalidate before using a cached response.
- no-store: Do not cache at all.
- max-age=3600: Cache for 1 hour.
- ETag and If-None-Match: Used for conditional requests. The server provides an ETag (a hash of the response), and the client sends it back with If-None-Match. If the content hasn’t changed, the server responds with 304 (Not Modified) and no body.
- Last-Modified and If-Modified-Since: Similar to ETag but based on timestamps. Less precise because clocks can drift.
- Expires: Older caching mechanism that works like max-age but with an absolute date. Still respected but mostly replaced by Cache-Control.
3. Headers for Conditional and Partial Requests
These headers help reduce payload size and improve performance. Useful for large responses or polling behavior.
- Range: Allows clients to request just a portion of a resource, often used for file downloads or video streaming. The server responds with 206 Partial Content.
- If-Modified-Since/If-None-Match: Used to validate cached data without downloading the full resource.
If the backend does not support these headers properly, clients may download full resources unnecessarily. Testers should verify that APIs behave correctly with Range and conditional headers especially when testing file downloads or resource-heavy endpoints.
4. Security and Auth Headers
Though not strictly about caching or content delivery, these are essential in controlling how data is sent and received securely.
- Authorization: Carries credentials like Bearer tokens or Basic Auth values.
- Cookie: Often carries session state.
- Origin/Referer: Sent by browsers to indicate where the request came from.
- Strict-Transport-Security, X-Content-Type-Options, X-Frame-Options: Control browser behavior for security.
How HTTPS Makes HTTP Secure
HTTPS is the secure version of HTTP. It uses TLS (Transport Layer Security) to encrypt data between the client and the server. While HTTP sends data in plaintext, HTTPS ensures that the information sent over the network is encrypted and can’t be read or modified by others.
Here’s how HTTPS adds security on top of HTTP:
- Encrypts all traffic so that no one in the middle can read or tamper with request or response data
- Authenticates the server using a digital certificate to prove the client is talking to the right endpoint
- Prevents data modification by ensuring that what the server sends is exactly what the client receives
- Protects credentials and sensitive data (like tokens, forms, or cookies) from being exposed in transit
- Supports HSTS (HTTP Strict Transport Security) so browsers remember to always use HTTPS for trusted domains
Common Security Threats in HTTP to Watch Out For
Using HTTP or even HTTPS incorrectly can leave gaps that attackers can exploit. Developers and testers need to know where those risks usually show up, especially in real-world deployments.
Here are some of the most common issues:
- Man-in-the-middle (MITM): Attackers intercept and possibly modify traffic between the client and server. This is easy when HTTP is used without TLS or when TLS is misconfigured.
- Header injection: If input is not sanitized correctly, attackers can insert CRLF (\r\n) characters to add malicious headers or alter response behavior. This can break response formatting or lead to cache poisoning.
- Cross-site scripting (XSS): Happens when user input is reflected back in responses without encoding. Attackers inject scripts into pages that get executed in the user’s browser.
- Cross-site request forgery (CSRF): Tricks users into making unintended requests while they are authenticated. For example, a hidden form on a malicious site submits a request to another site using the user’s session cookie.
- Information leakage: Detailed error messages, stack traces, or overly descriptive headers can reveal technology versions, internal endpoints, or server details that help attackers plan exploits.
- Downgrade attacks: These target clients that support both HTTP and HTTPS. Attackers intercept initial requests and force a fallback to plain HTTP, stripping away encryption. HSTS is one way to defend against this.
HTTP’s Role in API Calls and Microservice Communication
HTTP is the standard protocol used for communication between services. This includes browser-to-backend requests, mobile app calls, and internal service-to-service exchanges. In modern architectures like microservices, HTTP is the default layer for both public APIs and internal operations.
Here’s how HTTP typically fits into these scenarios:
- Request and response structure: Microservices use standard HTTP verbs such as GET, POST, PUT, and DELETE. These verbs describe what the service wants to do, such as reading, creating, updating, or deleting data.
- Stateless communication: Every HTTP request is independent and must carry all the context the server needs. This approach supports scaling and makes services easier to replace or upgrade.
- Context through headers: Headers carry additional data, such as Authorization for authentication, Content-Type to specify data format, and Correlation-ID for request tracing.
- Works with load balancers and retries: HTTP requests can pass through layers like gateways or reverse proxies that manage routing, retries, or rate limiting. These layers use headers and status codes to control behavior.
- Standard error signaling: HTTP status codes signal whether a request succeeded or failed. Clients use this information to decide what to do next. For example, a 503 might trigger a retry, and a 401 should trigger re-authentication.
- Internal service calls: Even inside a system, microservices often use REST or gRPC over HTTP. Some systems also use message queues, but control paths and admin calls usually go over HTTP.
Common Deployment Issues with HTTP
HTTP-based systems often behave differently in local development, staging, and production. Small differences in headers, redirects, or TLS handling can cause bugs that only appear after deployment. Testers and developers should watch for these common issues:
- Mixed content: A secure (HTTPS) frontend loads resources over plain HTTP. This is blocked by most browsers and breaks functionality like fonts, scripts, or images. This can be avoided by ensuring all resources are loaded over HTTPS and by enforcing content security policies that disallow insecure sources.
- Wrong base URLs: Environments use hardcoded or misconfigured base URLs. This causes API calls to point to localhost or staging endpoints in production, or vice versa. To avoid this, set environment-specific URLs using configuration files or environment variables, not embedded in code.
- TLS certificate issues: Expired, missing, or misconfigured SSL/TLS certificates cause failures in production. Some clients silently reject bad certificates, making the issue hard to detect unless explicitly tested. This can be prevented by using automated certificate monitoring, issuing valid certificates for staging, and enabling strict TLS validation in non-prod test environments.
- Redirect loops: HTTP to HTTPS redirects or www to non-www can conflict with application-level routing or load balancer settings, causing infinite redirect chains. This is usually resolved by centralizing redirect rules at the load balancer or CDN level and keeping application-level redirects minimal and consistent.
- Inconsistent HTTP headers: Security headers like Strict-Transport-Security, X-Frame-Options, or Content-Security-Policy are present in production but missing in staging or test. To solve this, these headers should be part of shared middleware or reverse proxy configuration that is applied consistently across all environments.
- Caching differences: Production environments often cache aggressively using CDNs or proxies, while staging environments may not. To avoid this, caching headers should be reviewed and tested explicitly in both staging and production.
- Proxy headers not trusted: If X-Forwarded-For or X-Forwarded-Proto are not handled correctly, services behind proxies may log wrong client IPs or assume an insecure connection. To fix this, proxies must be configured to add these headers, and backend services must explicitly trust only known proxy IP ranges.
How Requestly Helps with HTTP Debugging and Testing
Requestly is a developer tool that lets users intercept, modify, and debug HTTP traffic directly in the browser or across applications. Unlike browser dev tools, which are limited to passive inspection, Requestly gives testers and developers control over how HTTP requests and responses behave in real time without needing backend access.
Here’s how Requestly fits into debugging and testing workflows:
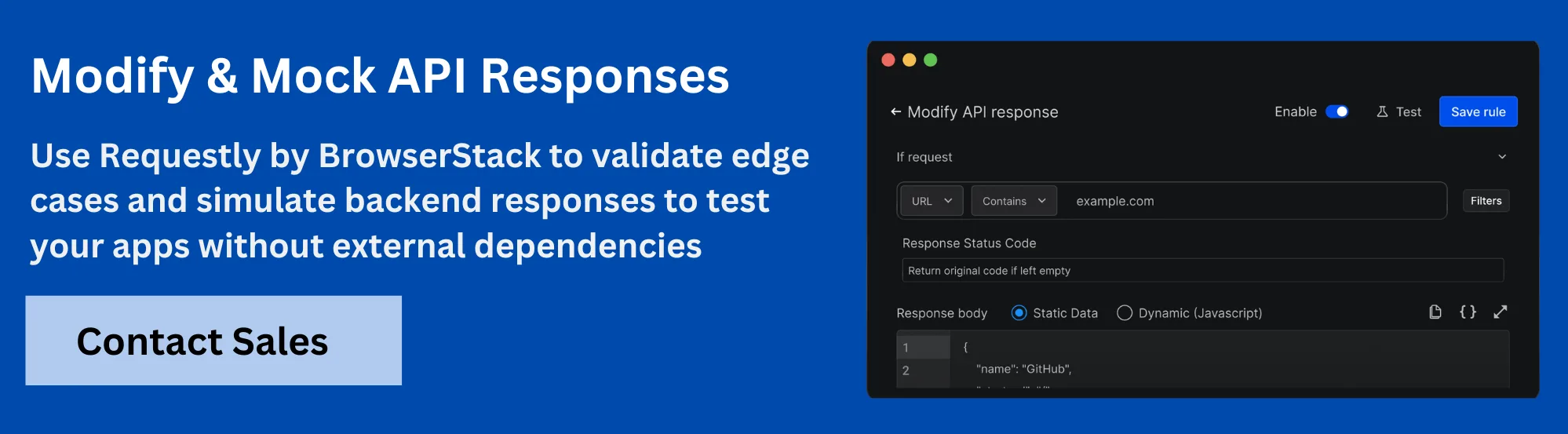
- Modify Headers: Add, remove, or change request and response headers to test how your application behaves under different client or server conditions.
- Mock API Response: Serve custom responses for specific endpoints to simulate backend behavior, inject test data, or trigger error flows.
- Redirect Request: Reroute HTTP requests from production or staging to local or alternate environments without touching the application code.
- Modify URL: Change query parameters, paths, or full URLs to test variations in routing, filtering, or pagination logic.
- Delay Request: Introduce network latency or server delay to simulate slow responses and test client timeout handling or loading states.
- Cancel Request: Block specific requests altogether to test fallback behavior, offline handling, or how the app recovers from missing resources.
- Modify Response: Change response body content in real time to simulate edge cases, test frontend behavior with malformed or partial data, or override fields temporarily.
Conclusion
HTTP defines how data moves between clients and servers through methods, headers, status codes, and caching rules. Methods control what operation is performed, headers carry metadata that changes how requests and responses are handled, status codes trigger specific client behavior, and caching rules decide whether responses are reused or fetched again.
Requestly gives you control over how HTTP behaves during testing. You can modify headers, mock responses, delay or block requests, and test how your app reacts to real-world conditions like API failures, network latency, or incorrect data. This removes dependency on backend changes and helps validate client-side logic with minimal setup.

Contents
- What Is HTTP?
- How HTTP Handles Requests and Responses
- HTTP Request Structure:
- HTTP Response Structure:
- Core HTTP Methods and Status Codes
- Common HTTP Methods:
- Common HTTP Status Codes:
- Role of Headers in Data Exchange and Caching
- 1. Headers That Control Content Negotiation
- 2. Headers That Affect Caching
- 3. Headers for Conditional and Partial Requests
- 4. Security and Auth Headers
- How HTTPS Makes HTTP Secure
- Common Security Threats in HTTP to Watch Out For
- HTTP’s Role in API Calls and Microservice Communication
- Common Deployment Issues with HTTP
- How Requestly Helps with HTTP Debugging and Testing
- Conclusion
Subscribe for latest updates
Share this article
Related posts
Get started today
Requestly is a web proxy that requires a desktop and desktop browser.
Enter your email below to receive the download link. Give it a try next time you’re on your PC!