HttpOnly Cookie: Benefits, Use Cases, and Best Practices


Cookies are small pieces of data that websites store in a user’s browser to manage sessions, track preferences, or enable personalized experiences. Among these, HttpOnly cookies have a specific purpose: they help protect sensitive data by restricting access from client-side scripts.
HttpOnly cookies are set by the server and are inaccessible to JavaScript running in the browser. This restriction reduces the risk of attacks like cross-site scripting (XSS), where malicious scripts try to steal session information or user credentials. While they do not replace other security measures, HttpOnly cookies form a critical part of a layered approach to protecting user data.
This article explains what HttpOnly cookies are, their benefits, implementation scenarios, and best practices for secure usage.
Understanding the HttpOnly Cookie
HttpOnly cookies are a type of browser cookie that the server sets with a special flag. This flag tells the browser to prevent client-side scripts from accessing the cookie. Unlike regular cookies, which can be read or modified through JavaScript, HttpOnly cookies remain accessible only to the server. This reduces exposure to attacks that target user session data.
The key concept behind HttpOnly cookies is limiting access to sensitive information. By keeping cookies out of reach from scripts running in the browser, applications can prevent common security risks.
Below are the main aspects that define HttpOnly cookies:
- Server-Side Access Only: The cookie can only be read and modified by the server, not by JavaScript.
- Session Management: Often used to store session identifiers securely.
- Security Flag: Works alongside other cookie flags like Secure, SameSite, and Domain to enhance protection.
- Persistent or Session-Based: Can be configured to expire when the browser closes or after a set duration.
Key Benefits of Using HttpOnly Cookies
HttpOnly cookies protect sensitive data by restricting access to the server side. They do not eliminate all risks, but they secure session identifiers and authentication tokens, making session hijacking much harder.
Below are the core benefits explained in detail:
- Mitigation of Cross-Site Scripting (XSS) Risks: HttpOnly cookies are inaccessible to JavaScript, which prevents attackers from stealing session tokens even if a script injection occurs. This reduces the attack surface without relying solely on input sanitization.
- Improved Session Security: Storing session identifiers in HttpOnly cookies ensures that server-side logic remains in control of session validation. Even if an attacker gains temporary access to the client, they cannot manipulate session data directly.
- Reduced Client-Side Exposure: Beyond XSS, restricting cookie access limits accidental leaks through browser extensions or embedded scripts that may interact with standard cookies.
- Compatibility with Additional Security Measures: HttpOnly works with Secure and SameSite flags to enforce HTTPS-only transmission and prevent cross-site request forgery (CSRF), creating a layered approach to cookie security.
- Predictable Behavior Across Browsers: Modern browsers consistently enforce the HttpOnly flag, ensuring that session management and authentication logic behave reliably without relying on client-side controls.
When and Why to Implement HttpOnly Cookies
HttpOnly cookies are essential whenever sensitive information must be protected from client-side scripts. They are most effective for session tokens, authentication data, and any server-managed state where security and integrity are critical. Implementing them strategically ensures both application security and consistent behavior across users.
Below are key scenarios with practical reasoning for using HttpOnly cookies:
- User Session Management: Store session identifiers in HttpOnly cookies. This prevents JavaScript or browser extensions from accessing session data, reducing the risk of session hijacking.
- Authentication Security: Use HttpOnly cookies for access tokens and login credentials. By restricting client-side access, these cookies protect authentication details from being exposed or tampered with.
- Preventing Cross-Site Request Forgery (CSRF): Combine HttpOnly with the SameSite flag for sensitive actions. This limits how cookies are sent in cross-site requests, blocking unauthorized requests from malicious sites.
- Server-Controlled Application State: Apply HttpOnly cookies when server-side validation or logic depends on critical data. This prevents clients from altering state and ensures consistent, predictable application behavior.
- Regulatory and Enterprise Compliance: Use HttpOnly cookies to meet security standards that require sensitive data to remain inaccessible from the client. This supports both internal security policies and external compliance mandates.
Step-by-Step Guide to Setting the HttpOnly Cookie
Setting an HttpOnly cookie involves configuring the server to include the HttpOnly flag when sending the cookie to the browser. This ensures that the cookie cannot be accessed by client-side scripts.
Below is a structured approach to implement HttpOnly cookies effectively.
Step 1: Identify Sensitive Data Determine which data needs protection. Typically, session identifiers, authentication tokens, and any server-managed state that impacts security or user access should be stored in HttpOnly cookies. This ensures that only critical information is protected while other non-sensitive cookies remain accessible if needed.
Step 2: Configure the Cookie on the Server Set the HttpOnly flag when creating the cookie on the server. The exact method depends on the server or framework being used. Setting this flag prevents client-side scripts from reading or modifying the cookie.
Step 3: Combine with Other Security Flags Add the Secure flag to ensure the cookie is sent only over HTTPS. Use the SameSite flag to restrict cross-site requests. These additional flags complement HttpOnly to reduce risks like eavesdropping, CSRF, and session hijacking.
Step 4: Set Expiration and Scope Define the cookie’s expiration based on the type of data. Session cookies should expire when the browser closes, while persistent cookies may have a defined lifespan. Limit the cookie’s scope using domain and path settings to prevent exposure across unrelated areas of the site.
Step 5: Test the Implementation After setting the cookie, verify that it is properly marked as HttpOnly and cannot be accessed through client-side scripts. Tools like browser developer consoles or automated testing solutions can confirm the cookie’s behavior. Testing ensures the intended security protections are in place.
Step 6: Monitor and Maintain Regularly review cookie settings and security flags, especially when updating authentication flows or server configurations. Monitoring ensures that HttpOnly cookies continue to protect sensitive data effectively as the application evolves.
Challenges and Limitations of HttpOnly Cookies
While HttpOnly cookies strengthen security, they are not a complete solution. Understanding their limitations is critical for implementing them effectively and avoiding false security assumptions. These challenges often arise from browser behavior, application architecture, and evolving attack methods.
Below are the key challenges and limitations to consider:
- Cannot Protect Against All Attacks: HttpOnly cookies block access from client-side scripts but do not prevent attacks that exploit server-side vulnerabilities, network interception, or social engineering. Developers must combine HttpOnly with other security measures.
- Limited Control in Client-Side Logic: Data stored in HttpOnly cookies is inaccessible to JavaScript, which can be restrictive if client-side scripts need to read or modify certain state information. Applications may need alternative approaches for client-side logic.
- Dependent on Browser Support: Most modern browsers enforce the HttpOnly flag consistently, but some older browsers or niche clients may ignore it. This can create inconsistencies in security across different user environments.
- Cannot Replace Strong Authentication: HttpOnly cookies secure session tokens but do not replace multi-factor authentication, strong password policies, or token expiration strategies. They are a complementary layer, not a primary defense.
- Potential for Misconfiguration: Improper combination of flags or incorrect domain/path settings can reduce the effectiveness of HttpOnly cookies, leaving sensitive data exposed. Careful configuration and testing are essential.
Best Practices for Ensuring Secure Use of HttpOnly Cookies
Implementing HttpOnly cookies correctly is essential for maximizing security while maintaining application functionality. Following best practices ensures that cookies remain effective in protecting sensitive data and integrating smoothly with other security measures.
Below are key best practices with clear reasoning:
- Always Use the HttpOnly Flag for Sensitive Cookies: Apply the HttpOnly flag to all cookies storing session tokens, authentication data, or any sensitive server-managed state. This prevents client-side scripts from accessing critical information.
- Combine with Secure and SameSite Flags: Use the Secure flag to enforce HTTPS transmission and the SameSite flag to restrict cross-site requests. This layered approach mitigates risks such as eavesdropping and CSRF attacks.
- Limit Scope with Domain and Path Settings: Restrict cookies to the specific domain and path where they are needed. This reduces exposure and prevents cookies from being sent in unintended contexts.
- Set Appropriate Expiration: Define expiration times based on the sensitivity and purpose of the cookie. Session cookies should expire when the browser closes, while persistent cookies should have a clearly defined lifespan to minimize risk.
- Regularly Test Cookie Behavior: Use browser developer tools or automated testing frameworks to verify that HttpOnly cookies cannot be accessed by client-side scripts. Regular testing ensures that configuration changes do not weaken security.
- Monitor and Update Configurations: Review cookie settings whenever authentication flows or server configurations change. Ongoing monitoring helps maintain consistent security as the application evolves.
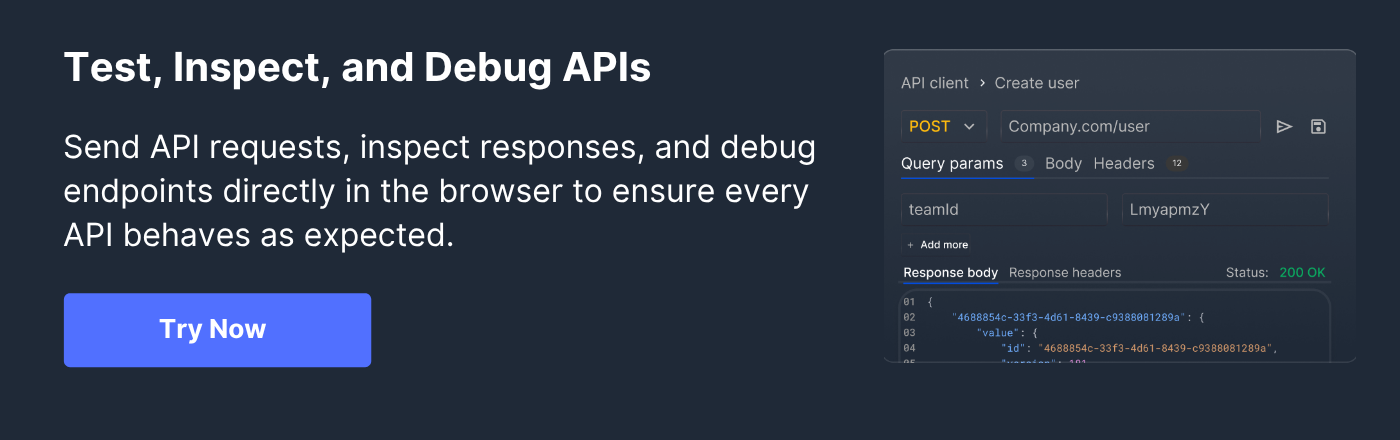
Why Use Requestly to Test HttpOnly Cookie Functionality
Requestly is a browser-based tool that lets developers and testers intercept, inspect, and modify HTTP requests and responses without changing the backend. It can be used to validate cookie attributes, test server-side behavior, and simulate different scenarios to ensure HttpOnly cookies are configured and functioning correctly.
Here are some ways to test HttpOnly cookies using Requestly:
- Inject and Modify Set-Cookie Headers: Requestly allows you to modify HTTP headers, including the Set-Cookie header, enabling you to test how your application handles cookies during development or debugging.
- Simulate Client-Side Access Attempts: While HttpOnly cookies prevent client-side scripts from accessing them, it’s crucial to verify that this protection is in place. Requestly helps you simulate scenarios where scripts attempt to access these cookies, ensuring that they are properly protected.
- Verify Cookie Attributes: Use Requestly to inspect Set-Cookie headers and confirm that HttpOnly and Secure flags are set correctly. This helps ensure that cookies are configured to prevent unauthorized access and transmission over insecure channels.
- Combine with Automation for Regression Testing: Integrate HttpOnly cookie checks into automated tests to catch configuration or behavior changes during application updates. This ensures security is maintained over time.
Common Misconceptions About HttpOnly Cookies
HttpOnly cookies are often misunderstood, which can lead to misconfigurations or security gaps during testing and implementation.
Below are common misconceptions with explanations and practical implications:
- HttpOnly cookies do not block all attacks: They prevent client-side script access but do not protect against CSRF, server-side exploits, or network interception. Testers should verify additional protections like SameSite, HTTPS, and server-side validation.
- JavaScript cannot read HttpOnly cookies: Any functionality requiring client-side access must use separate non-sensitive cookies. Testers should confirm that scripts cannot access protected cookies.
- HttpOnly cookies do not replace strong authentication: Session tokens remain secure, but passwords, multi-factor authentication, and token expiration must still be enforced. Testers should verify these layers remain intact.
- Browser behavior is not uniform: Most modern browsers enforce HttpOnly, but some older or niche browsers may ignore it. Testers should validate cookies across supported browsers.
- HttpOnly alone does not prevent CSRF: Combine it with SameSite flags and server-side CSRF protections. Testers should simulate cross-site requests to confirm protections.
- Misconfigured cookies remain exposed: Incorrect domain, path, or Secure settings can make cookies vulnerable. Testers should inspect actual requests to ensure proper configuration.
Conclusion
HttpOnly cookies protect sensitive data by restricting access from client-side scripts, reducing the risk of session hijacking and other attacks. They work best when combined with Secure, SameSite, and proper server-side session management, forming a layered approach to application security.
Testing HttpOnly cookies with Requestly allows developers and testers to inspect cookie attributes, simulate client-side access attempts, and validate server-side handling. This ensures that cookies are configured correctly, behave consistently across environments, and maintain the intended security protections.

Contents
- Understanding the HttpOnly Cookie
- Key Benefits of Using HttpOnly Cookies
- When and Why to Implement HttpOnly Cookies
- Step-by-Step Guide to Setting the HttpOnly Cookie
- Challenges and Limitations of HttpOnly Cookies
- Best Practices for Ensuring Secure Use of HttpOnly Cookies
- Why Use Requestly to Test HttpOnly Cookie Functionality
- Common Misconceptions About HttpOnly Cookies
- Conclusion
Subscribe for latest updates
Share this article
Related posts