Complete Guide to X-XSS-Protection and Web Security


Your lightweight Client for API debugging
No Login Required
Requestly is a web proxy that requires a desktop and desktop browser.
Enter your email below to receive the download link. Give it a try next time you’re on your PC!










Cross-Site Scripting (XSS) remains one of the most common vulnerabilities in modern web applications, allowing attackers to inject malicious scripts into web pages viewed by users. These scripts can steal sensitive information, manipulate content, or perform unauthorized actions on behalf of users.
The X-XSS-Protection header is a legacy HTTP response header designed to control the browser’s built-in XSS filtering mechanisms. It provides an additional layer of defense by instructing compatible browsers to detect and block certain types of XSS attacks before they can execute.
This article explains the purpose, implementation, and testing of X-XSS-Protection headers, along with strategies to enhance overall web security.
What is XSS Protection Header
Cross-Site Scripting (XSS) attacks occur when malicious scripts are injected into web pages, allowing attackers to steal data, manipulate content, or perform actions on behalf of users. Web browsers provide built-in XSS filters to help mitigate these risks, but developers can control their behavior using the X-XSS-Protection header.
The Role of the X-XSS-Protection Header
Web browsers include built-in XSS filters that detect suspicious scripts and prevent them from executing. The X-XSS-Protection header allows web developers to control how these filters behave, adding an extra layer of defense against client-side attacks. While not a replacement for comprehensive security measures like Content Security Policy, it acts as a first line of protection, particularly for older browsers.
- Enable or disable browser XSS filters: Developers can explicitly turn the browser’s XSS protection on (1) or off (0) depending on their security requirements.
- Block malicious scripts: The 1; mode=block directive stops the page from rendering if an XSS attack is detected, preventing execution of harmful code.
- Improve legacy browser security: Many older browsers still rely on this header as a primary safeguard against reflected XSS attacks.
- Support layered security: By combining X-XSS-Protection with input validation and CSP, applications can achieve a multi-layered defense against XSS threats.
Benefits of XSS Protection Header
Enabling the X-XSS-Protection header offers more than just basic browser filtering. It provides targeted mitigation against common XSS attacks while complementing other security measures.
Here are some of the key benefits that make it a valuable addition to web security:
- Mitigates reflected XSS attacks: Prevents scripts injected via URLs, query parameters, or form inputs from executing, reducing the risk of data theft and session hijacking.
- Enhances legacy browser security: Older browsers without full CSP support can still enforce XSS filtering through this header, maintaining compatibility while improving security.
- Blocks page rendering on detected attacks: With mode=block, the header stops the page from rendering entirely when suspicious scripts are detected, preventing accidental exposure of sensitive information.
- Supports layered security strategy: Complements input validation, output encoding, and CSP by providing a client-side safety net against XSS attacks.
- Reduces developer overhead for basic XSS protections: Enables browser-level protections without requiring complex server-side logic for every input or output vector.
- Improves user trust and browsing safety: By preventing malicious scripts from executing, users experience safer interactions with the application, strengthening brand credibility.
Understanding Different XSS Attack Types
Cross-Site Scripting attacks come in several forms, each exploiting web application vulnerabilities differently. Understanding these types is essential for implementing effective XSS protections, including X-XSS-Protection headers and complementary measures like Content Security Policy.
1. Reflected XSS
Occurs when malicious scripts are embedded in URLs or form inputs and immediately reflected back in the server’s response. These attacks typically require the victim to click a crafted link, and X-XSS-Protection can block script execution in compatible browsers. For example, a search input that echoes user input without proper sanitization can be exploited.
2. Stored XSS
Involves malicious scripts being permanently stored on the server, such as in databases or comment sections, and served to multiple users. X-XSS-Protection can help mitigate some cases, but server-side validation and output encoding are crucial for full protection.
3. DOM-based XSS
Happens entirely on the client side when JavaScript manipulates the DOM using untrusted input. Since the attack occurs in the browser without a new server response, X-XSS-Protection may not detect it, highlighting the need for secure coding practices and CSP.
4. Mutated XSS
Also known as mXSS, this occurs when browsers automatically “fix” malformed HTML or JavaScript, unintentionally executing injected scripts. Browser filters, including X-XSS-Protection, can catch some mutated scripts, but careful input handling is essential.
Content Security Policy (CSP) and X-XSS-Protection
While the X-XSS-Protection header provides browser-level defenses against certain XSS attacks, Content Security Policy (CSP) offers a more comprehensive and flexible approach. CSP allows developers to define which sources of content are trusted, controlling scripts, styles, images, and other resources loaded by the browser.
Here are the key ways CSP complements X-XSS-Protection:
- Complementary roles: X-XSS-Protection acts as a reactive filter that blocks detected scripts, while CSP is proactive, preventing untrusted scripts from executing in the first place.
- Script source control: CSP can restrict inline scripts and external sources, reducing the likelihood of both reflected and stored XSS attacks.
- Mitigation of DOM-based XSS: Unlike X-XSS-Protection, CSP can prevent many DOM-based attacks by enforcing strict script loading policies.
- Reporting and monitoring: CSP supports reporting violations to a specified endpoint, helping teams detect and analyze potential attack attempts.
- Fallback protection: For browsers that do not fully support CSP, X-XSS-Protection can provide a minimal level of filtering as a secondary safeguard.
Integrating XSS Protection in Your Web Development Workflow
Securing web applications against XSS attacks requires a structured approach. Following clear steps ensures that X-XSS-Protection headers and complementary security measures are consistently applied throughout the development lifecycle.
Step 1: Configure X-XSS-Protection Header
Set X-XSS-Protection: 1; mode=block in your server responses for pages handling user input. This enables browser-level filtering and blocks detected attacks.
Step 2: Implement Content Security Policy (CSP)
Define trusted sources for scripts, styles, and other resources. CSP prevents untrusted code from executing and mitigates many XSS attack vectors.
Step 3: Sanitize User Input
Validate and encode all user-supplied data before processing or rendering it. This prevents malicious scripts from entering the application.
Step 4: Review Third-Party Scripts
Audit external libraries and embedded scripts for potential vulnerabilities before including them in your pages. Only use trusted and actively maintained resources.
Step 5: Integrate Security Checks into CI/CD
Automate scanning for missing headers, unsafe scripts, and other XSS risks during build and deployment. This ensures issues are caught early.
Step 6: Educate the Development Team
Train developers on secure coding practices, common XSS patterns, and the proper use of headers like X-XSS-Protection and CSP.
Advanced XSS Protection Strategies
Beyond basic headers and input sanitization, advanced XSS protection involves proactive and layered defenses that address sophisticated attack vectors. These strategies help secure applications against emerging threats and reduce reliance on a single security measure.
Here are some advanced approaches to enhance XSS protection:
- Context-aware output encoding: Encode data differently depending on where it is used in HTML, JavaScript, URL, or CSS contexts to prevent script execution in any scenario.
- Strict Content Security Policies: Use CSP with nonce or hash values for inline scripts and avoid unsafe-inline directives to tightly control script execution.
- HTTP-only and Secure cookies: Protect session cookies from being accessed by scripts, reducing the impact of XSS attacks on user sessions.
- Subresource Integrity (SRI): Validate external scripts by including cryptographic hashes to ensure only the expected code is executed.
- Regular security audits: Continuously review application code, dependencies, and server configurations to identify new XSS vulnerabilities.
- Use of security-focused frameworks: Adopt frameworks and libraries that automatically handle output encoding, templating, and sanitization to minimize developer error.
- Automated XSS scanning and fuzzing: Implement tools to simulate attacks and detect weak points in input handling and output rendering.
When to Use Content Security Policy (CSP) vs. X-XSS-Protection
Both X-XSS-Protection and Content Security Policy (CSP) serve to protect web applications from XSS attacks, but they operate differently and are suitable for distinct scenarios. Understanding when to use each ensures optimal security without redundancy.
Here are the guidelines for choosing between them:
- Use X-XSS-Protection for legacy browser support: Older browsers that do not fully support CSP can still enforce basic XSS filtering using this header.
- Use CSP for modern, comprehensive protection: CSP allows fine-grained control over script execution, inline scripts, and external resources, effectively mitigating reflected, stored, and DOM-based XSS attacks.
- Combine both for layered security: Enabling X-XSS-Protection alongside CSP provides a fallback mechanism for browsers that only partially support CSP or have it disabled.
- Rely on CSP for complex applications: Applications with dynamic content, third-party scripts, or multiple content sources benefit more from CSP’s detailed controls.
- Prefer X-XSS-Protection for quick mitigation: For small-scale or legacy projects where implementing CSP fully may be challenging, X-XSS-Protection offers immediate, low-overhead defense.
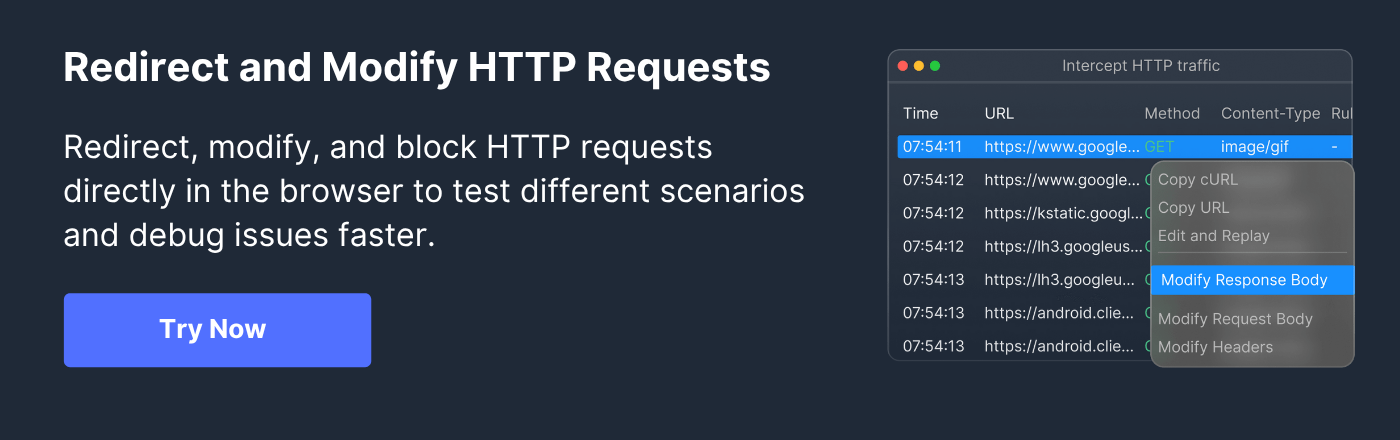
How Requestly Facilitates XSS Protection Testing
Requestly is a versatile testing and debugging tool that allows developers and testers to intercept, modify, and manipulate HTTP requests and responses in real time. It enables testing XSS protections by simulating malicious inputs, altering headers, and observing how the application responds to potential attacks.
Here are the key features of Requestly that help test XSS protection effectively:
- Modify Headers: Add or change the X-XSS-Protection header in server responses to test how browsers enforce XSS filtering.
- Inject Test Scripts: Insert malicious scripts into requests to simulate reflected and stored XSS attacks safely.
- Intercept Requests: Capture and examine requests and responses to identify missing headers or improperly sanitized input.
- Redirect Requests: Redirect requests to test how different endpoints handle malicious inputs or altered headers.
- Automate Test Scenarios: Create rules that automatically inject payloads or modify headers across multiple pages to streamline testing.
- Validate Browser Behavior: Observe how the browser reacts to different header configurations and script injections to confirm protections are working.
Conclusion
X-XSS-Protection remains a valuable tool in securing web applications against common XSS attacks, particularly in legacy browsers. When combined with proper input validation, output encoding, and Content Security Policy, it strengthens the overall security posture and helps prevent malicious scripts from compromising user data or application functionality.
Requestly enhances this process by allowing developers and testers to simulate attacks, modify headers, and observe browser behavior in real time. This ensures that security measures are properly implemented and provides actionable insights for improving application defenses.

Contents
- What is XSS Protection Header
- The Role of the X-XSS-Protection Header
- Benefits of XSS Protection Header
- Understanding Different XSS Attack Types
- Content Security Policy (CSP) and X-XSS-Protection
- Integrating XSS Protection in Your Web Development Workflow
- Advanced XSS Protection Strategies
- When to Use Content Security Policy (CSP) vs. X-XSS-Protection
- How Requestly Facilitates XSS Protection Testing
- Conclusion
Subscribe for latest updates
Share this article
Related posts
Get started today
Requestly is a web proxy that requires a desktop and desktop browser.
Enter your email below to receive the download link. Give it a try next time you’re on your PC!