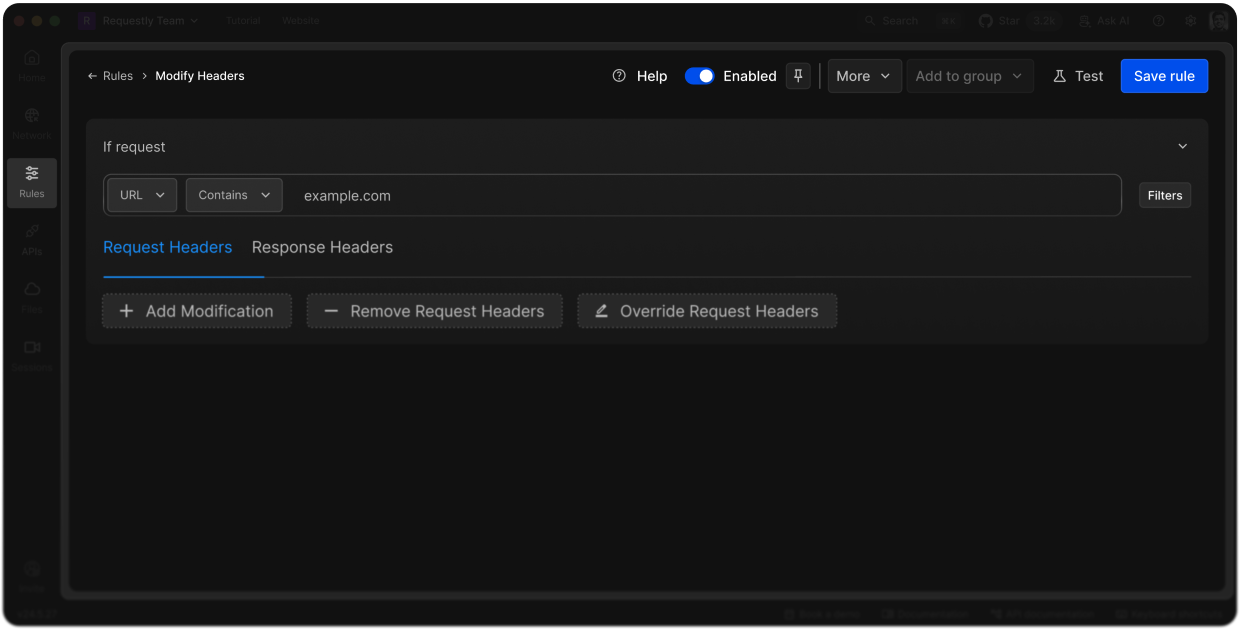
ModHeader slowing you down with ads ?
Unlike ModHeader, Requestly is an ad-free, open-source dev tool built for real developers and QA teams. It intercepts, modifies, and mocks HTTPs traffic in real time, both in-browser and on your desktop apps.
Fast & Powerful
One-click import
Enterprise-grade
24/7 Expert help
Requestly is a web proxy that requires a desktop and desktop browser.
Enter your email below to receive the download link. Give it a try next time you’re on your PC!










Why choose Requestly over Modheader
Requestly is a modern, open-source, browser-first tool that goes beyond header editing, no complex setup, no trust issues, and packed with features for both developers and teams.
No ads, No Spam, and We’re Open Source
Requestly is a web proxy that requires a desktop and desktop browser.
Enter your email below to receive the download link. Give it a try next time you’re on your PC!












Forever Free HTTP Header Modifications
Gentle Learning Curve
Simple, Fast & Powerful than ModHeader
Collaboration & 1-Click Sharing
Popular Use Cases
Modify/ Bypass CORS
Bypass CORS errors during development by modifying response headers locally, without changing anything on the server.
Set Authorization Header
Inject auth tokens into request headers to test APIs without logging in or changing your code.
Modify Cookie Header
Add, modify, or remove Cookie headers in requests to fake sessions, test edge cases, or debug issues, no need to touch your browser storage.
Migrate from Modheader to Requestly in a single click
Import your Modheader configurations to Requestly with 1-click and enhance your web development experience. Click the button below to start a the process.
Frequently Asked Questions
What is Requestly and how is it different from ModHeader ?
Requestly is a powerful HTTP interception and mocking tool that lets you intercept, record, and mock HTTP requests on the fly. While ModHeader is limited to modifying headers, Requestly goes much further, allowing you to redirect URLs, override API responses, inject scripts, block requests, and collaborate with your team using a modern UI.
Is Requestly more secure than ModHeader?
Is Requestly open-source
Is Requestly free to use ?
Yes. Requestly offers a Free plan with essential features like unlimited header rules and standard HTTP modifications, perfect for getting started.
Does Requestly offer an enterprise plan?
Yes. Requestly offers an Enterprise Plan built for larger teams and organizations that need full control and compliance. It includes unlimited usage, API access, SSO & SAML, GDPR and SOC 2 compliance, user access management, SLAs for support and uptime, invoice-based billing, and priority support via Slack Connect, Email, and Chat.
Is Requestly free for students?
Yes! Requestly is free for students, enjoy access to powerful tools and features with no cost.
Why are my response header modifications not visible in the browser’s dev tools?
Why Aren’t My Requestly Rules Working?
How do I modify headers using Requestly?
Can I apply header modifications to specific HTTP methods (GET, POST, etc.)?
Yes, you can apply header modifications to specific HTTP methods by specifying the method condition within the rule settings. This ensures that headers are modified only for requests of certain types. For a detailed guide,.
Can I import my ModHeader settings directly into Requestly?
| Features | ModHeader | Requestly |
|---|---|---|
| No Ads, No Spam | ||
| HTTP Header Modification | ||
| Modify API Response | ||
| URL Redirects & Modification | ||
| Page-level Filters | ||
| Open Source | ||
| Collaboration | ||
| Enterprise Features (SSO, RBAC, Auditing) | ||
| Support |
Built for teams
Effortless team collaboration
Quick One time sharing
Team workspaces
Export data & sync to Git
Secure and private
Enterprise-ready security and compliance

SOC-II Compliance
Single Sign-On (SSO)
Role-based access control
Data encryption
Audit logs
Regular security updates