Requestly a better alternative to HTTP Toolkit
Looking for a modern alternative to HTTP Toolkit? Requestly offers a browser-first, open-source solution that simplifies development and testing with unmatched speed and flexibility
Trusted by 300,000+ developers from Fortune 500 companies.
Simple, fast & powerful
Requestly is a web proxy that requires a desktop and desktop browser.
Enter your email below to receive the download link. Give it a try next time you’re on your PC!











No context switching
Requestly is a web proxy that requires a desktop and desktop browser.
Enter your email below to receive the download link. Give it a try next time you’re on your PC!










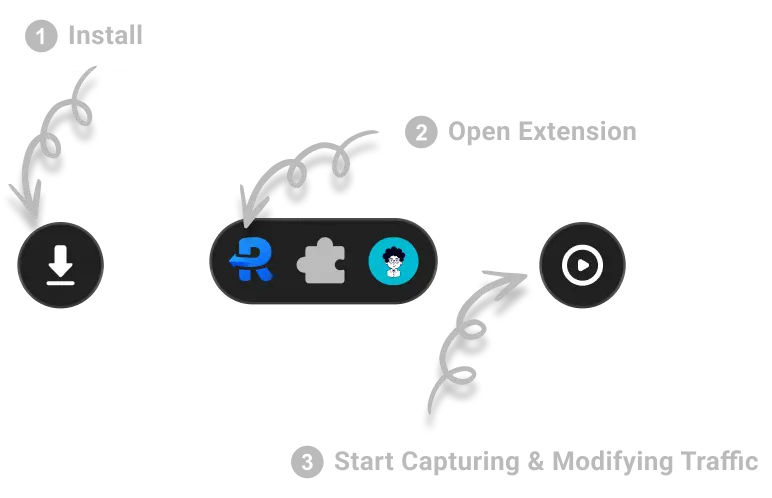
Zero setup
Requestly is a web proxy that requires a desktop and desktop browser.
Enter your email below to receive the download link. Give it a try next time you’re on your PC!










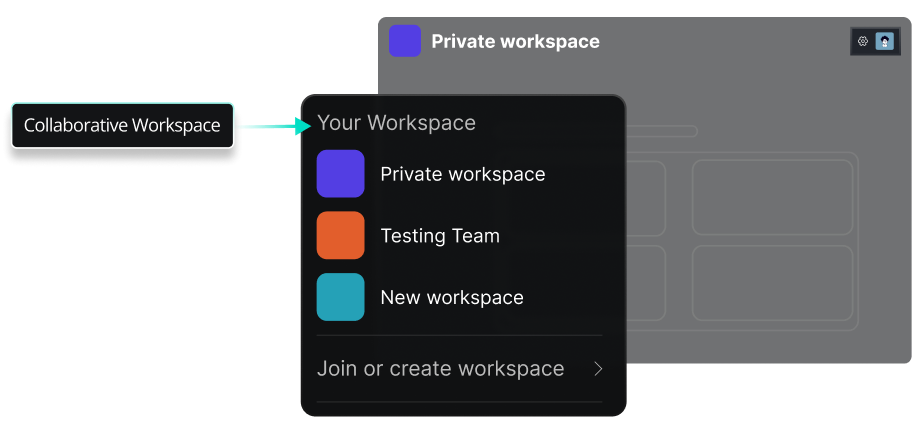
Collaboration
Requestly is a web proxy that requires a desktop and desktop browser.
Enter your email below to receive the download link. Give it a try next time you’re on your PC!










Best customer support

Enterprise Ready
Requestly is a web proxy that requires a desktop and desktop browser.
Enter your email below to receive the download link. Give it a try next time you’re on your PC!











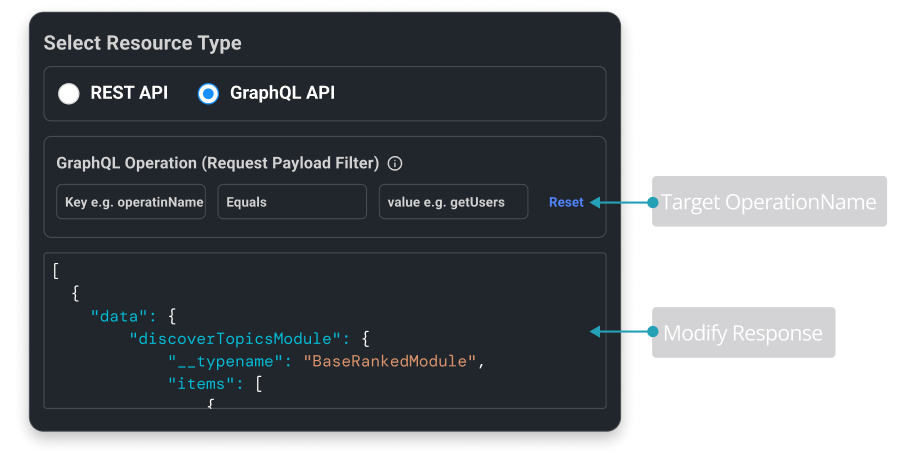
GraphQL Support
Requestly is a web proxy that requires a desktop and desktop browser.
Enter your email below to receive the download link. Give it a try next time you’re on your PC!










| Features | HTTP Toolkit | Requestly |
|---|---|---|
| Zero Proxy & VPN Issues | ||
| Lightweight | ||
| Modify HTTP headers | ||
| Modify API response | ||
| Modify URL | ||
| GraphQL support | ||
| Inject Scripts | ||
| Page level filters | ||
| Collaboration | ||
| Breakpoints | ||
| Mock server | ||
| Capture browser sessions | ||
| API client | ||
| Open source | ||
| Enterprise-ready | ||
| Support |
Built for teams
Effortless team collaboration
Quick One time sharing
Team workspaces
Export data & sync to Git
Secure and private
Enterprise-ready security and compliance

SOC-II Compliance
Single Sign-On (SSO)
Role-based access control
Data encryption
Audit logs
Regular security updates





