Requestly a better alternative to Proxyman
Proxyman, for macOS, intercepts and edits HTTP/HTTPS requests. Requestly, as a browser extension and app, offers URL modification, script injection, API mocking, and session recording.
Trusted by 300,000+ developers from Fortune 500 companies.
Unlike Proxyman, Requestly offers a modern interface with advanced features like cloud sync, collaboration, and regex support for seamless rule management
Simple, fast & powerful
Requestly provides a user-friendly and modern interface curated by UX experts. Requestly is available in two forms — a browser extension & a desktop application for all major platforms like Chrome & Chrome-based browsers, Firefox, Safari, Edge, Brave, Opera, Vivaldi, Windows, Mac(Apple & Intel Chips), and Linux
Requestly is a web proxy that requires a desktop and desktop browser.
Enter your email below to receive the download link. Give it a try next time you’re on your PC!










No context switching
Requestly is available as a browser extension on all major Chrome, Firefox, Edge, and all other Chromium-based browsers. No need to switch context to any other application
Requestly is a web proxy that requires a desktop and desktop browser.
Enter your email below to receive the download link. Give it a try next time you’re on your PC!










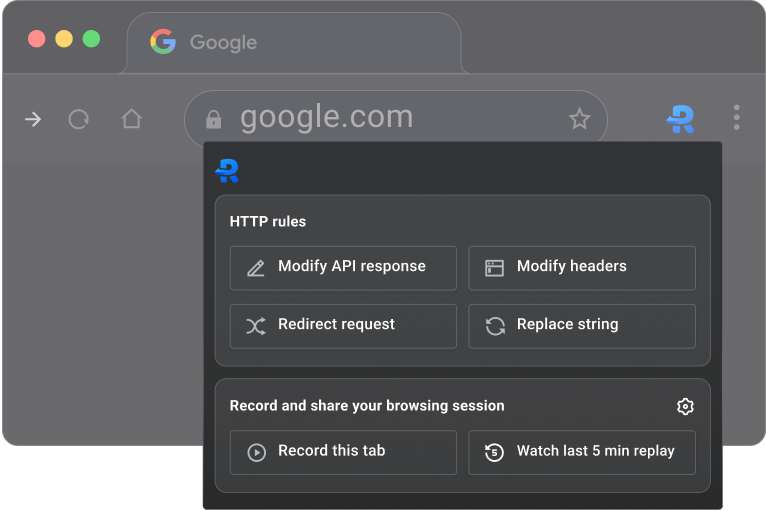
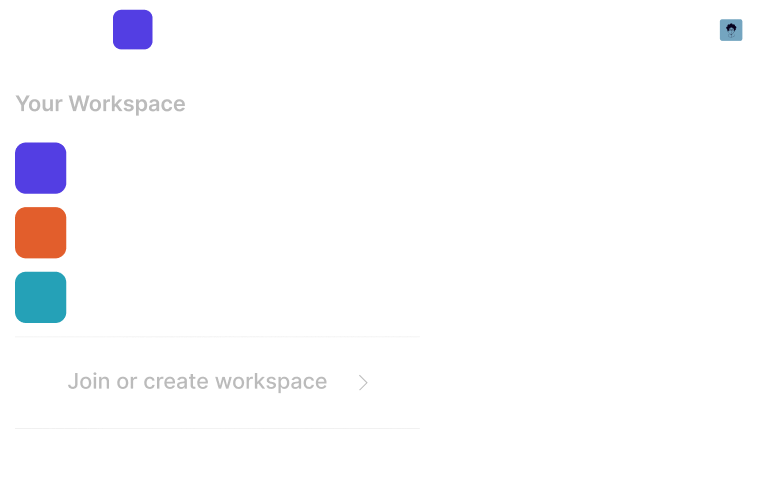
Collaboration
Requestly is designed for teams and, hence, makes collaboration very smooth. You can work with your team in a common/shared workspace. You can also create and share groups for easy organization of HTTP rules.
Requestly is a web proxy that requires a desktop and desktop browser.
Enter your email below to receive the download link. Give it a try next time you’re on your PC!










Best customer support
Requestly is known to provide the best customer support to its customers. Requestly has more than 1000 reviews on the Chrome Store testifying the best support from the Requestly team.
Requestly is a web proxy that requires a desktop and desktop browser.
Enter your email below to receive the download link. Give it a try next time you’re on your PC!










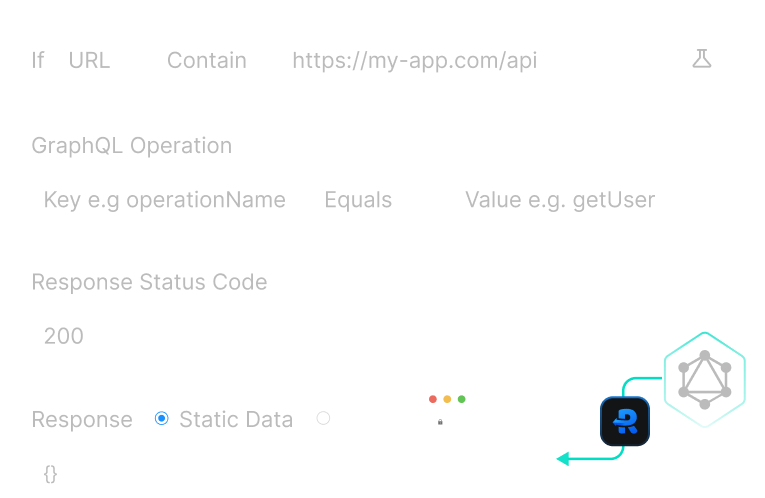
GraphQL Support
Requestly offers exclusive GraphQL support, unlike proxyman, which is tailored for REST APIs and struggles with GraphQL's schema-based structure, requiring extra filtering for specific operations.
Requestly is a web proxy that requires a desktop and desktop browser.
Enter your email below to receive the download link. Give it a try next time you’re on your PC!










| Features | Proxyman | Requestly |
|---|---|---|
| Zero Proxy & VPN Issues | ||
| Lightweight | ||
| Modify HTTP headers | ||
| Modify API response | ||
| Modify URL | ||
| GraphQL support | ||
| Inject Scripts | ||
| Page level filters | ||
| Collaboration | ||
| Breakpoints | ||
| Mock server | ||
| Capture browser sessions | ||
| API client | ||
| Open source | ||
| Support |
Built for teams
Effortless team collaboration
Quick One time sharing
Team workspaces
Export data & sync to Git
Secure and private
Enterprise-ready security and compliance

SOC-II Compliance
Single Sign-On (SSO)
Role-based access control
Data encryption
Audit logs
Regular security updates





